.webp?width=2000&height=484&name=SmBanners-04%20(11).webp)

Cyber Risk Consulting -
Assessment Services
K logix's assessments deliver exactly what you need - a clear plan to improve and continue to protect your organization. Our assessments focus on both business and security, delivering results you can share with executives to gain their mindshare and buy-in.
K logix's Cyber Risk Consulting Assessment Services
Provides strategic and tactical recommendations to address any areas of weakness.
- Each assessment is custom tailored to your needs
- Recommendations that are business-friendly, using business language
- Focused on driving the ongoing advancement of your security strategy

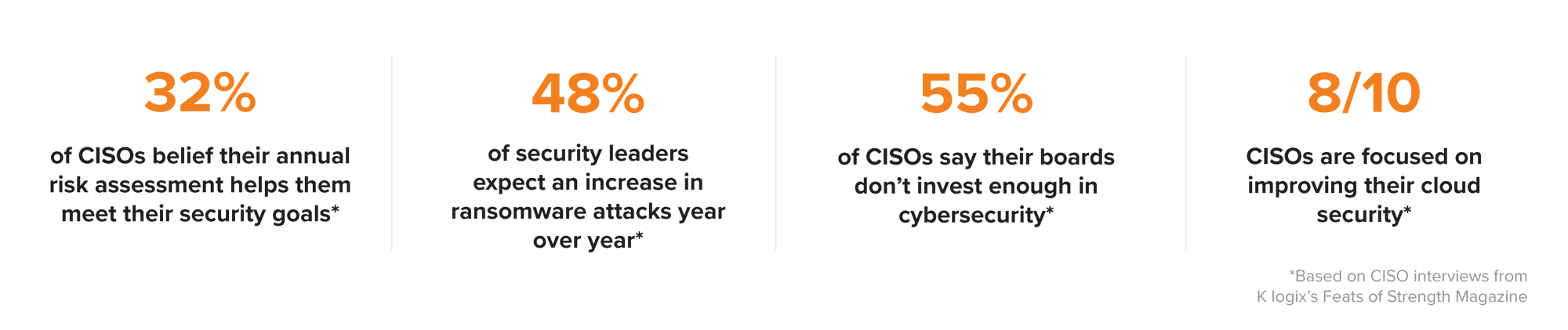
WHAT THE INDUSTRY SAYS

Examples of Cyber Risk Consulting Assessment Services
Our Assessment Services go beyond the examples below and extend to any security program area, so reach out to us to discuss your specific challenge!
AI Impact Assessment
![]()
-
Analyze your AI maturity across technical, organizational, and cultural dimensions to reveal strengths and gaps
-
Map your current state against industry frameworks and readiness models for a clear benchmark
-
Recommend strategic and tactical actions aligned with business objectives to reduce AI-related risks
-
Deliver a visually driven roadmap that helps executives and technical teams prioritize and act with confidence
Risk Assessment
![]()
- Align security program risk to an industry-standard framework like NIST, ISO, or CIS
- Receive strategic and tactical recommendations to address security program gaps, areas of strength, and deliver a clearly defined roadmap
- Turn threat and impact into business-friendly language and results
- Mature and reduce risk with an actionable plan, aligned to your specific goal
Framework Assessment
![]()
-
Align to a framework: NIST, ISO, CIS Controls, HIPAA, Pre-SOC
- Manage risks and opportunities associated with AI by aligning to: NIST AI RMF, ISO/IEC 42001
-
Receive strategic and tactical recommendations to address security program gaps, areas of strength, and deliver a clearly defined roadmap
-
Get a better understanding of your maturity against a framework and identify key gaps that need addressing
Ransomware & Threat Assessments
![]()
-
Custom tailored to address the most impactful threats facing your organization
-
Participate in interviews to take a business-case driven approach to combatting threats
-
Extensive review and workshopping led by our threat experts
-
Receive a detailed look at your maturity against threats, such as measuring against the NIST CSF Ransomware Framework for any Ransomware Assessment
WHAT OUR EXPERTS DELIVER
Narrative Report PDF
Identified common theme risk areas and executive-friendly findings and recommendations
Engagement PowerPoint
Includes detailed findings summarizing strength areas, opportunities for improvement, and more
Executive PowerPoint
High-level view of findings tailored for executive audiences
Six Month To-Do Lists
Areas to take immediate action including foundational security program areas and tactical risk mitigation items
