Diving into the mind of a ransomware actor: what will the 2023 threat landscape bring?
January is a time for us to reflect on our past year and our goals for 2023. As I sat back and contemplated the new year, I wondered what the 2023 goals for malicious cyber actors would be? I know … it’s a question on everyone’s minds. To answer this, let’s think like a Threat Intelligence Analyst and take a peek.
The Four Types of Threat Intelligence: Strategic, Tactical, Technical, and Operational
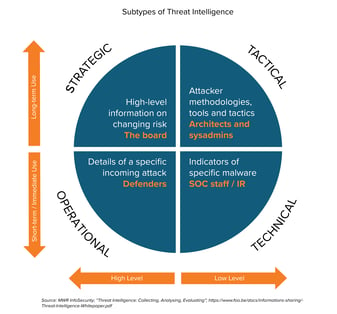
Cyber threat intelligence is a recurring process where analysts continually strive to understand adversaries’ motives, tactics, and techniques. This process can help identify the likely threats an organization may face by demystifying the types of adversaries targeting an industry and how those adversaries conduct their attacks. Organizations can then utilize this knowledge to devise a cybersecurity strategy that addresses and mitigates the most pertinent threats.
There are four types of threat intelligence: strategic, tactical, technical, and operational. Strategic and tactical threat intelligence are the areas K logix best helps customers. Organizations can utilize strategic and tactical threat intelligence for long-term planning to build a forward-thinking and resilient cybersecurity program.
- Strategic threat intelligence is a high-level overview of the threats an organization may confront, meant for consumption by an executive audience.
- Tactical threat intelligence dives deeper into the tactics, techniques, and procedures (TTPs) employed by malicious actors and is digested by security-minded personnel.
Technical and operational threat intelligence are meant for short-term consumption as the relevancy of findings fade quickly.
- Analysts conducting technical threat intelligence dig for clues that indicate an attack has occurred, known as indicators of compromise (IOCs).
- Operational threat intelligence is the high-level information of an attack, such as timing and how it unfolds*.
A Ransomware Group’s 2023 To-Do List
A recurring statistic in cybersecurity reports is that ransomware has been steadily proliferating and will continue to be a top threat in 2023, which is why K logix decided to dive into the minds of ransomware actors to identify three goals that could be on their 2023 to-do list:
- Utilize the data exfiltration tactic (MITRE TA0010) more often.
- Dedicate more time and resources to targeting cloud environments.
- Increase exploitation of third-party vulnerabilities for initial access into an organization.
As ransomware actors plan their 2023 strategy, expertly employing the data exfiltration tactic will be a top priority. This objective is already exhibiting itself in the ransomware world. Ransomware actors are starting to utilize the double extortion technique where they 1) encrypt data and 2) exfiltrate that data. This places additional pressure on the victim to pay the ransom to prevent sensitive or proprietary data from being released. It also offers ransomware actors additional sources of revenue beyond the targeted victim. A rival business may pay a large sum for its competitor’s data. There may also be geopolitical motives for intellectual property to cross country lines, making data exfiltration a profitable and alluring tactic.
With more organizations storing their critical data in the cloud, ransomware actors are adapting as any profitable business would by shifting their gaze to where the critical data and profits reside – the cloud. Historically, ransomware groups have targeted on-premises IT infrastructure, but in 2023 ransomware groups will aim to target unsecure cloud environments**. Prominent threat actors such as TeamTNT (allegedly retired in 2021) and WatchDog have already been targeting cloud environments. K logix predicts that ransomware actors will draw inspiration from them in 2023 to target organization’s cloud environments more effectively.
The risk of third-party vulnerabilities has been echoed across security reports this past year and for good reason. According to IBM’s Cost of a Data Breach Report 2022, vulnerabilities in third-party software were one of the top four initial attack vectors in 2022. This was also IBM’s finding in 2021. Exploiting third-party vulnerabilities for initial access enables ransomware groups to 1) scale, targeting more organizations with less effort, and 2) focus their time and resources on improving other tactics such as exfiltration, which is why K logix believes this is likely an initial attack vector that ransomware groups will seek to make more use of in 2023.
How Should Organizations Prepare for Threats?
Organizations can prepare for the 2023 threat landscape by:
- Building a strong identity and access management program
- Reviewing cloud environment configurations
- Implementing an endpoint detection and response tool
- Developing mature third-party risk management processes
- Conducting a threat intelligence assessment
For more information and how K logix can help organizations prepare for the 2023 threat landscape, contact one of our experts: info@klogixsecurity.com.
Sources:
*https://www.eccouncil.org/cyber-threat-intelligence/
**https://unit42.paloaltonetworks.com/ransomware-in-public-clouds/