SASE Assessment
Determine your SASE readiness through our easy 5 minute assessment. You’ll discover your current maturity and what steps to take to achieve a successful SASE architecture.
When you’ve completed it, you’ll instantly see your SASE maturity level.
Core Security
How are these core security technologies deployed? Core security technologies must be in place before moving towards a SASE architecture.
| 1. API Gateway | |||||
| 2. Email Gateway (with link sandboxing) | |||||
| 3. Remote Browser Isolation (RBI) | |||||
| 4. Endpoint Detection and Response (EDR) | |||||
| 5. Network Detection and Response (NDR) | |||||
| 6. Extended Detection and Response (XDR) | |||||
| 7. Security Information and Event Manager (SIEM) | |||||
| 8. Security Orchestration Automation and Response | |||||
| 9. Identity as a Service (IDaas) | |||||
| 10. Intelligent User and Entity Behavior Analytics (UEBA) |
-
1. API Gateway
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
-
2. Email Gateway (with link sandboxing)
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
-
3. Remote Browser Isolation (RBI)
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
-
4. Endpoint Detection and Response (EDR)
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
-
5. Network Detection and Response (NDR)
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
-
6. Extended Detection and Response (XDR)
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
-
7. Security Information and Event Manager (SIEM)
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
-
8. Security Orchestration Automation and Response
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
-
9. Identity as a Service (IDaas)
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
-
10. Intelligent User and Entity Behavior Analytics (UEBA)
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
CNAPP
Cloud Native Application Protection Platform technologies are cloud native and look for misconfigurations in the cloud tenant that could cause security risks. Let us know if you own any of the following.

|
||
|---|---|---|
| 1. Cloud Security Posture Management (CSPM) | ||
| 2. Cloud Workload Protection Platform (CWPP) | ||
| 3. Kubernetes Security Posture Management (KSPM) | ||
| 4. Cloud Infrastructure Entitlement Management (CIEM) | ||
| 5. SaaS Security Posture Management (SSPM) | ||
| 6. Security Information and Event Manager (SIEM) | ||
| 7. Infrastructure as Code (IaC) |
-
1. Cloud Security Posture Management (CSPM)
- Ownership
- No Ownership
-
2. Cloud Workload Protection Platform (CWPP)
- Ownership
- No Ownership
-
3. Kubernetes Security Posture Management (KSPM)
- Ownership
- No Ownership
-
4. Cloud Infrastructure Entitlement Management (CIEM)
- Ownership
- No Ownership
-
5. SaaS Security Posture Management (SSPM)
- Ownership
- No Ownership
-
6. Security Information and Event Manager (SIEM)
- Ownership
- No Ownership
-
7. Infrastructure as Code (IaC)
- Ownership
- No Ownership
SD-WAN
Software defined wide area networking (SD-WAN) is a core component of SASE. It is a software-based approach leveraged by SASE to monitor and manage connectivity with dispersed data centers, offices and edges.
Is SD-WAN deployed in your environment?
How is SD-WAN deployed in your environment?
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
Next Gen-SWG
A cloud access security broker is a cloud service that sits between cloud service users and cloud applications (SaaS applications) to monitor all activity and enforce security policies within the application.
Is Secure Web Gateway deployed in your environment?
How is your Secure Web Gateway deployed?
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
Cloud Access Security Broker (CASB)
A cloud access security broker is a cloud service that sits between cloud service users and cloud applications (SaaS applications) to monitor all activity and enforce security policies within the application.
Is Cloud Access Security Broker deployed in your environment?
How is Cloud Access Security Broker (CASB) deployed in your environment?
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
DLP
DLP is a solution that monitors ingress and egress traffic, blocking traffic that contains sensitive information that could lead to a data breach or leak.
Is Data Loss Prevention deployed in your environment?
How is Data Loss Prevention (DLP) deployed in your environment?
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
Zero Trust
Zero Trust is a core component of the Security Service Edge (SSE) side of a SASE architecture. Through SASE, zero trust becomes flexible and easier to manage.
Is Zero Trust Network Access (ZTNA) deployed in your environment?
How is ZTNA deployed in your environment?
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
Firewall
Firewalls are instrumental to detecting and preventing network based attacks, how are your firewalls deployed?
Is a firewall deployed in your environment?
How is security cloud firewall deployed in your environment?
- Cloud
- On-Prem
- Hybrid
- No Ownership
- Not in environment or unsure
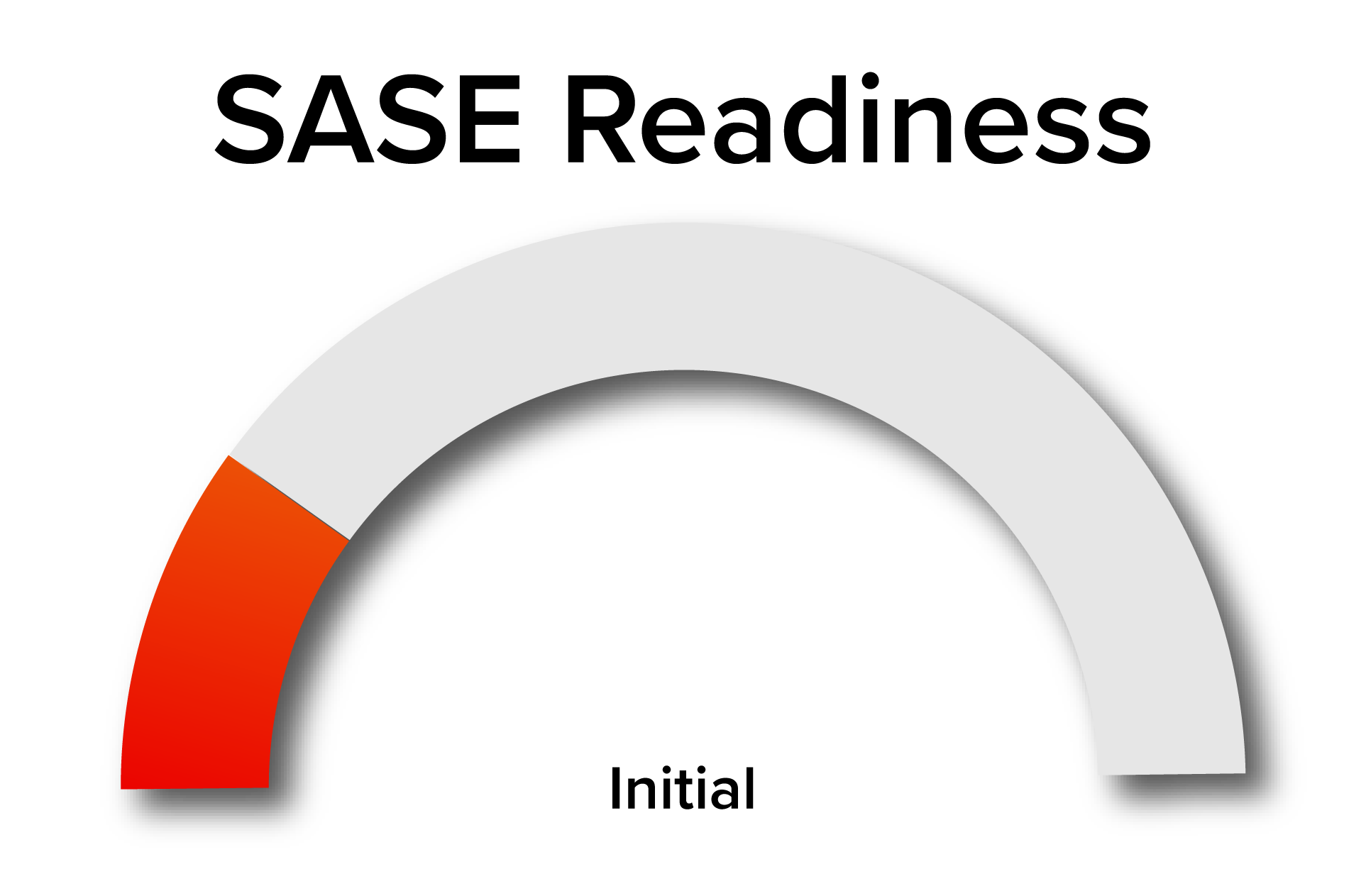
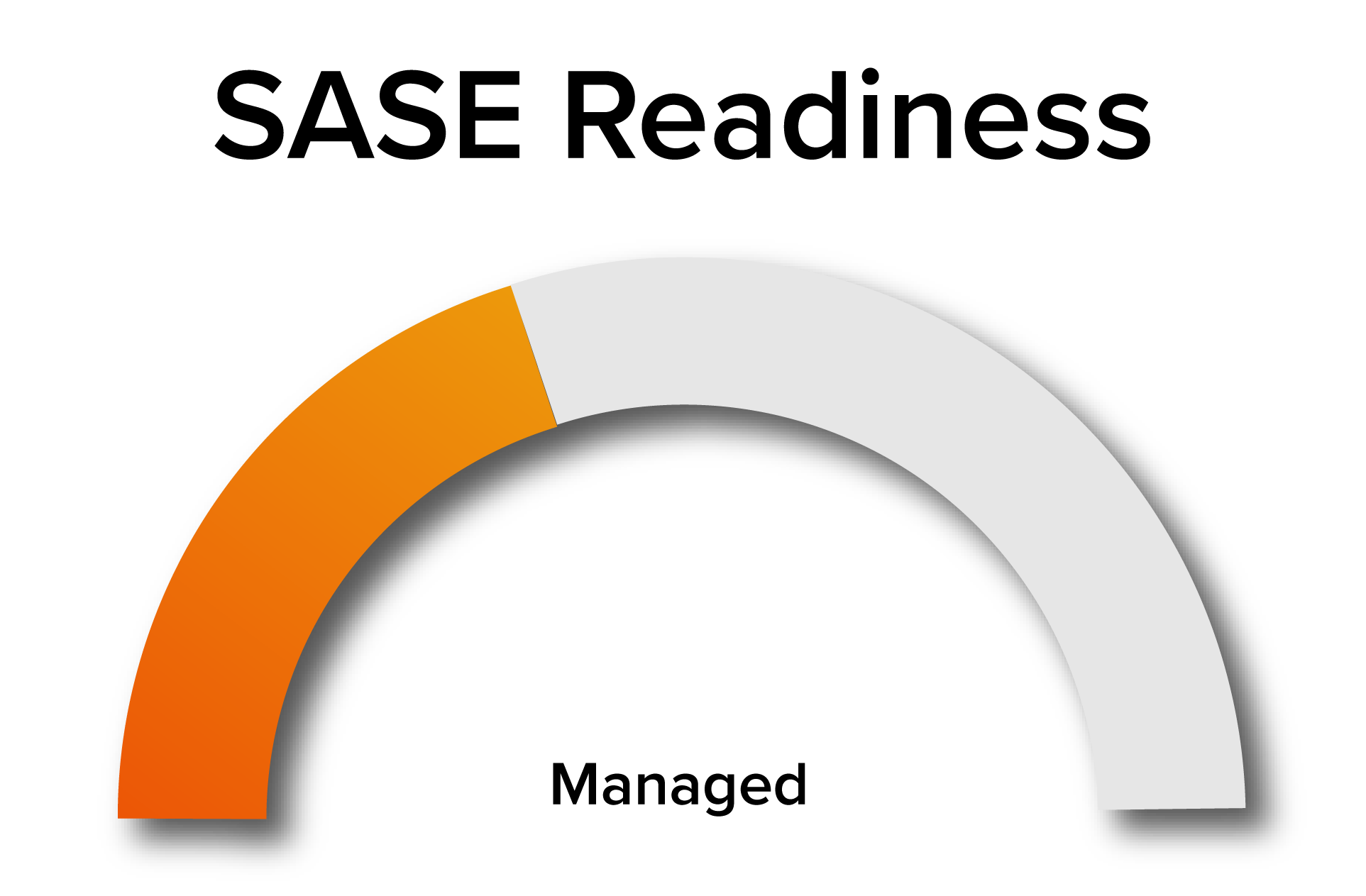
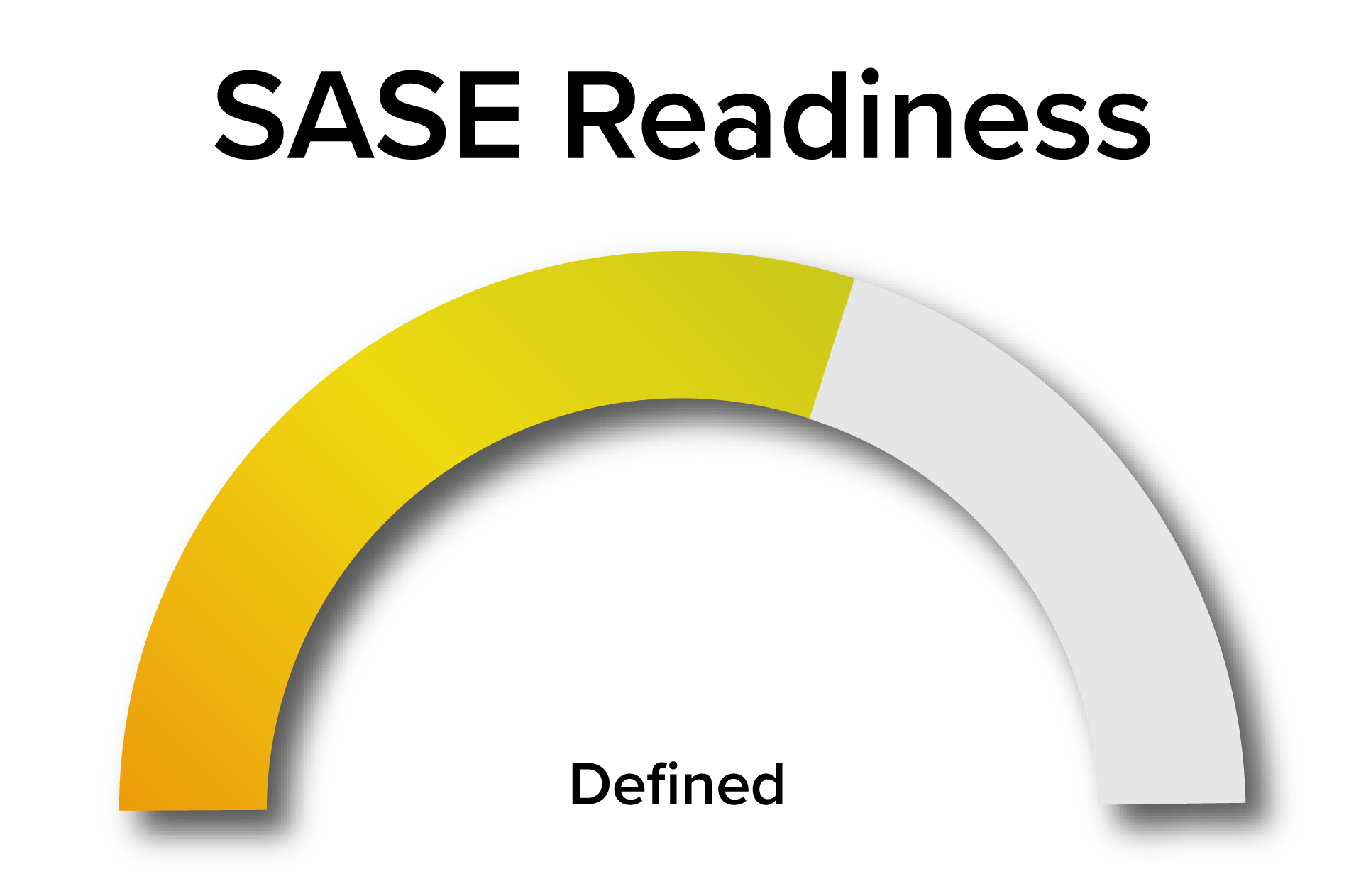
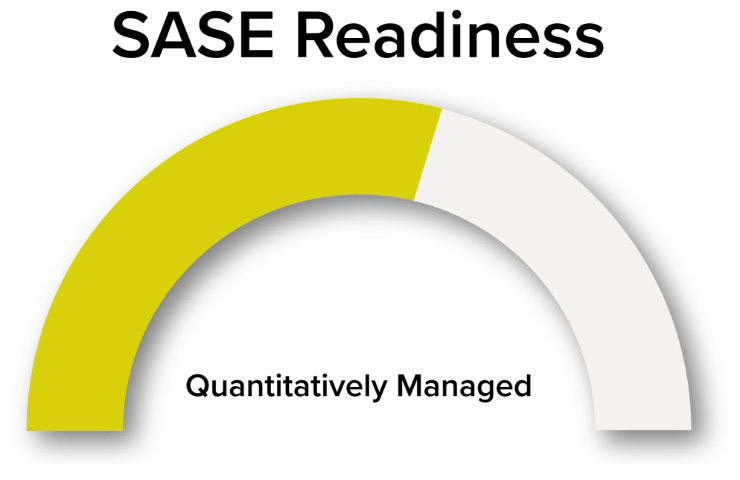
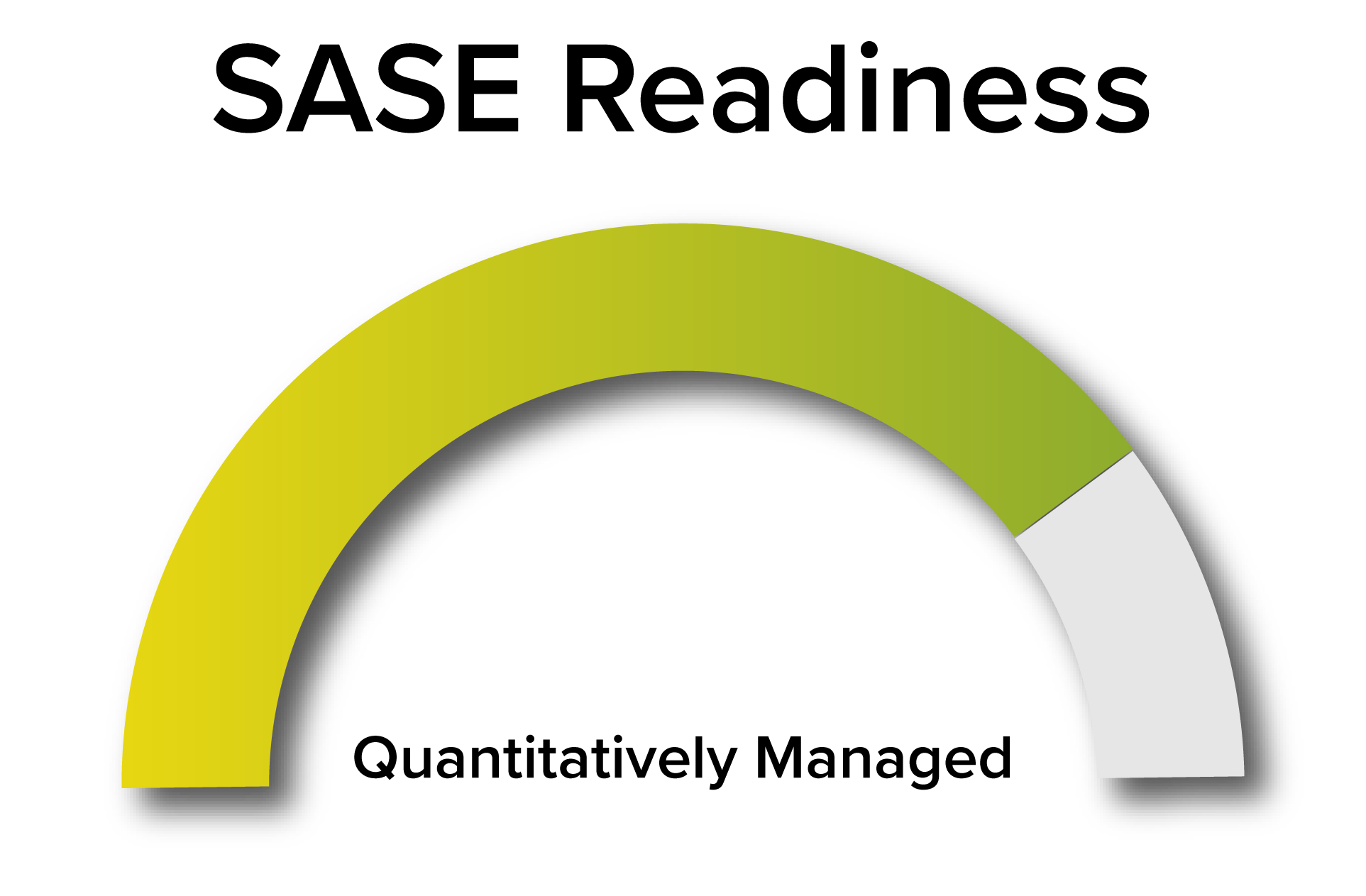
Thank you!
Congrats for completing the assessment, here is your SASE maturity. To access your personalized in-depth SASE report, please complete the form below.
Simplify SASE with K logix
Take the next step with your SASE readiness results
SASE Educational Session
Educate yourself, your team, and/or your executives with a customized in-depth SASE/SSE education session. Sessions may be tailored according to your SASE Readiness results, specific focus areas, and more.
SASE Program Session
Receive an in-depth assessment of your current maturity and actionable next steps to achieve a SASE architecture. Address and align to your specific requirements while identifying gaps and how to address them.
SASE Technology Session
Leverage K logix’s agnostic research to determine the best fit SASE technology. Clear the noise of cluttered SASE technologies.