The Strategic Guide to the MITRE ATT&CK Framework
Published On: December 9, 2020
Updated: September 12, 2025
Who is MITRE?
Before diving into the framework, let's take a high-level look at MITRE and why they continue to be central to many organizations’ threat modeling, detection, and response strategies.
MITRE is a federally funded research organization that maintains and curates the ATT&CK framework gathering data from real-world threat actors, collaborative community input, red team / blue team activities, and more to help defenders identify, detect, and respond to adversarial behavior.
In 2011, Lockheed Martin adapted the military “kill chain” concept to cyber operations proposing that attacks follow a linear sequence of phases (Reconnaissance → Weaponization → Delivery → Exploitation → Installation → Command & Control → Actions on Objective). While this model remains influential, its assumptions (including strict sequence, perimeter first defenses, etc.) are increasingly challenged by modern, non-linear adversarial behavior especially in cloud, hybrid, and zero-trust architectures.
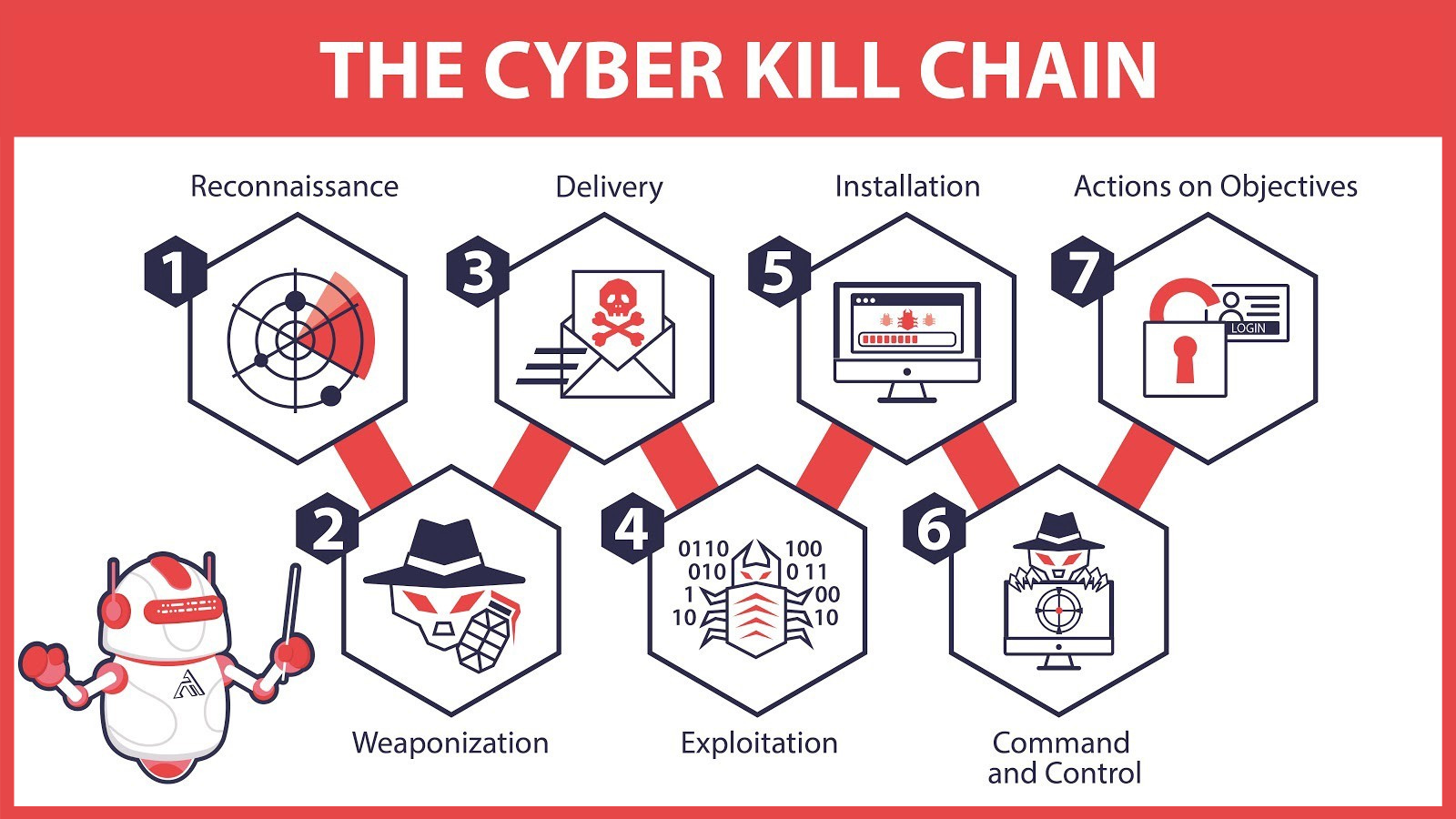
(image by Medium)
In 2013, MITRE expanded its scope by introducing the Enterprise ATT&CK framework, which catalogs adversary behavior in terms of Tactics, Techniques, and Procedures (TTPs). While earlier emphasis was often on post-initial access behaviors, ATT&CK now also includes earlier-stage activity (like reconnaissance, resource development) and captures newer platforms such as ESXi hypervisors, containers, and cloud services. This evolution supports defenders adopting zero-trust and dynamic detection models where attacks don’t always follow a strict linear path.
MITRE’s focus on post-exploitation detection has led to innovative threat hunting based on attack behaviors rather than attack signatures. These adversarial behaviors collectively make up the MITRE ATT&CK framework. ATT&CK stands for: Adversarial Tactics, Techniques & Common Knowledge.
What is ATT&CK?
The MITRE ATT&CK framework remains a globally accessible knowledge base of adversary tactics, techniques, and procedures (TTPs), drawn from real-world observations. In particular, the Enterprise matrix serves as a foundation for modeling threats across common operating systems, cloud, containers, ESXi hypervisors, network devices, and identity providers. ATT&CK breaks out behavior not only into techniques but also sub-techniques for added granularity.
Before ATT&CK, many threat hunting efforts leaned heavily on signature-based detection (anti-virus, IDS) or static Indicators of Compromise (IoCs). Modeling adversary behavior with TTPs shifts the focus toward detecting consistent, observable patterns that persist even as tools or infrastructure change. This approach is especially powerful now, as attackers frequently deviate from linear attack lifecycles, using parallel or overlapping techniques, and operating across multiple platforms.
-png.png)
(a sampling of the tactics and techniques that represent the MITRE ATT&CK® Matrix for Enterprise)
Tactics represent the adversary’s objective: the “why” behind each technique or sub-technique in the ATT&CK framework. In Enterprise ATT&CK v17, there are 14 tactics, including Reconnaissance, Initial Access, Resource Development, Defense Evasion, Credential Access and others. Each tactic captures a strategic goal adversaries pursue such as discovering information, maintaining access, elevating privileges, or exfiltrating data.
Techniques describe how adversaries pursue those goals. Within each tactic you’ll find multiple techniques and many of those are broken out into sub-techniques for finer granularity. For example, under the Credential Access tactic, “Brute Force” is a technique, and sub-techniques include Password Guessing, Password Spraying, Credential Stuffing, etc. Likewise, moving laterally (the Lateral Movement tactic) might use techniques like Remote Service Session Hijacking, Pass the Ticket, or Exploitation of Remote Services, depending on platform and context.
What differentiates ATT&CK from other evaluation frameworks?
The MITRE ATT&CK framework remains dynamic and flexible, with frequent updates driven by the cybersecurity and threat intelligence community to reflect the latest adversary behaviors. While it built on concepts from the Cyber Kill Chain,ATT&CK addresses several blind spots:
Attack source: The Cyber Kill Chain assumed all threats originated outside the protected network and the attack passed through a perimeter defense, such as a firewall. The ATT&CK framework assumes adversaries may already be inside and maps well to Zero Trust Architecture (ZTA) models, where internal monitoring is critical.
Attack sequence: The Cyber Kill Chain assumed all attacks would follow an ordered sequence of steps. The ATT&CK framework allows for the complexity associated with advanced threat tactics which may not follow an ordered sequence.
Attack detection: ATT&CK emphasizes detecting behaviors inside the environment and reducing adversary dwell time or Mean Time to Respond (MTTR), rather than assuming all attacks can be blocked at the firewall.
Attack groups: ATT&CK tracks over 150 named threat groups, each mapped to observed behaviors. For example, APT29 continues to evolve, most recently associated with campaigns against cloud and SaaS environments. This behavioral mapping helps defenders anticipate techniques without relying solely on attribution.
What challenges does the framework address and how can organizations make sense of the findings?
MITRE is considered vendor-agnostic and does not compete with or endorse any vendor solution. In its ATT&CK Evaluations, MITRE acts as an independent third party, emulating adversary behaviors while vendors demonstrate their detection and response capabilities. These exercises go beyond traditional red team/blue team simulations, but the concept of purple teaming (where offensive and defensive teams collaborate to validate and improve defenses) remains central.
Each evaluation round is scoped to a finite set of adversary behaviors tied to a specific threat group or campaign. For example, recent evaluations have emulated groups such as Wizard Spider, Sandworm, and OilRig, reflecting the evolving threat landscape across endpoint, cloud, and managed service environments.
Rather than assigning scores, MITRE categorizes how detections occur using a mix of visibility and analytic categories, sometimes with modifiers that add context. This approach helps organizations understand detection quality and coverage, not just whether a vendor triggered an alert.
Security teams use the evaluation results as a common reference point to compare vendors, assess coverage gaps, and strengthen their own threat detection strategies. In addition, ATT&CK remains a foundational language for red, blue, and purple teams, helping defenders model adversarial behaviors and test their resilience against real-world tactics and techniques.
K logix and MITRE ATT&CK
K logix’s Research Department conducts independent, vendor-agnostic evaluations of security technologies to help organizations identify the best solutions for their unique needs. By leveraging frameworks like MITRE ATT&CK and analyzing market trends, our team provides objective insights that empower leaders to make confident, future-ready security investments.
Subscribe
Stay up to date with cyber security trends and more

