Last week F5 released an update to its BIG-IP product, patching a vulnerability affecting the iControl REST API. This is significant because there is a strong likelihood of abuse for remote code execution (RCE).
According to F5: This vulnerability may allow an unauthenticated attacker with network access to the BIG-IP system through the management port and/or self IP addresses to execute arbitrary system commands, create or delete files, or disable services. There is no data plane exposure; this is a control plane issue only.
To determine if your product and version have been evaluated for this vulnerability, refer to the Applies to (see versions) box on their dedicated resource page. For more information about security advisory versioning, refer to K51812227: Understanding security advisory versioning.
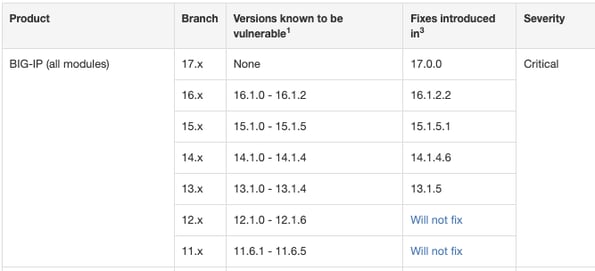 (Source: https://support.f5.com/csp/article/K23605346)
(Source: https://support.f5.com/csp/article/K23605346)
On their site, they provide recommended actions for patching. We want to stress the importance of network segmentation, as this particular item is likely to be abused if segmentation to the management interface on the device is not properly isolated.
Additional reference material may be found here:
ISC: https://isc.sans.edu/forums/diary/F5+BIGIP+Unauthenticated+RCE+Vulnerability+CVE20221388/28624/
F5 Support: https://support.f5.com/csp/article/K23605346
If you have any questions or concerns, don't hesitate to reach out to K logix: info@klogixsecurity.com.