Updated on: September 3, 2025
Identity and Access Management (IAM) is a key word that we’ve been hearing in the cybersecurity space for years now, addressing the “how” for user access permissions to resources. In 2025, this extends beyond human users to include non-human identities such as service accounts, bots, API keys, and other machine identities. The focus on managing the access of people, these non-human entities, digital identities, and privileged accounts has increased significantly to address modern risks, putting IAM at the forefront of identity programs within companies today.
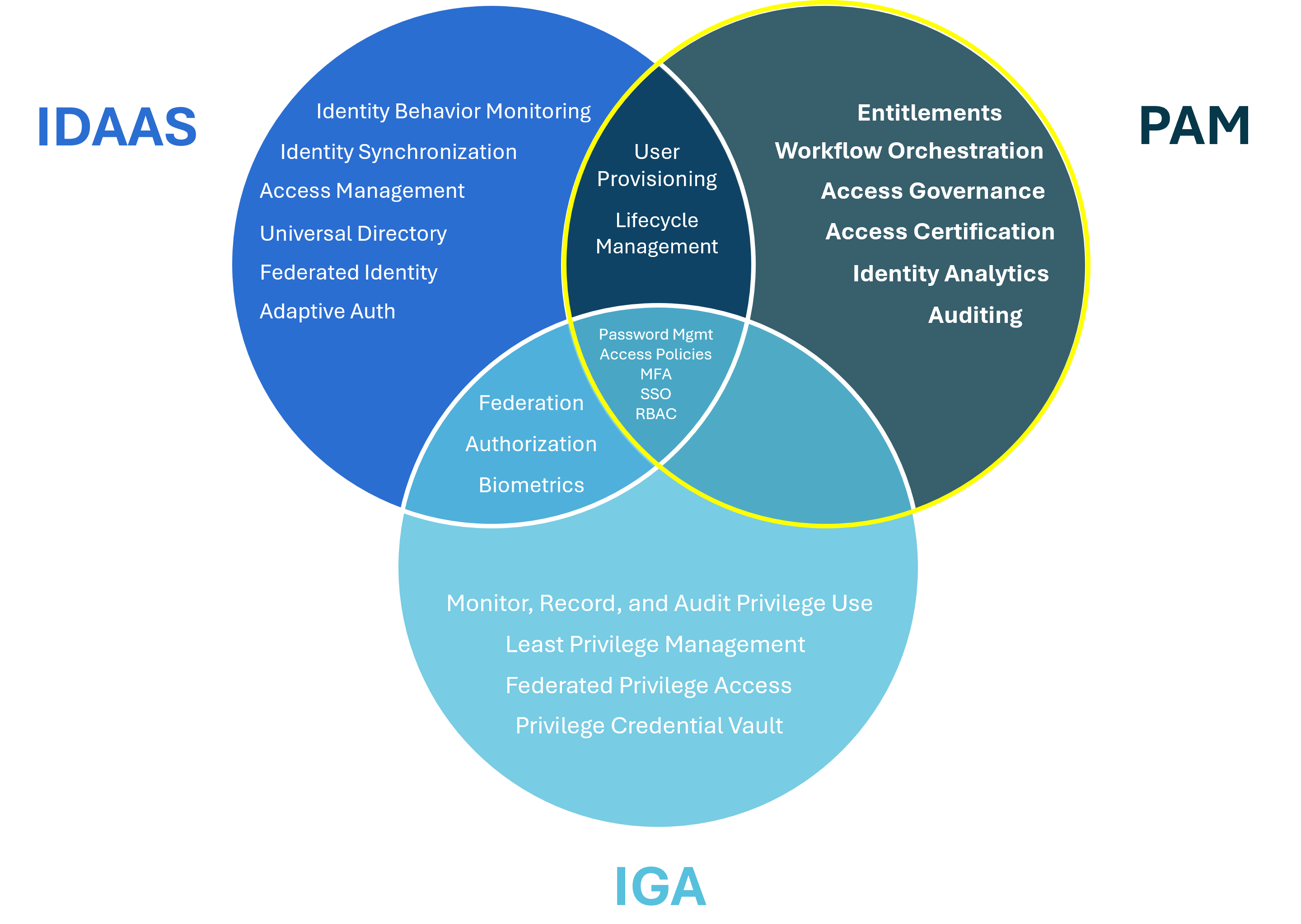
IAM programs work to reduce access risks specifically related to identity. With the growth of hybrid and distributed workforces, the importance of properly managing identities has become even more critical, requiring organizations to explore new solutions that minimize disruptions in users’ ability to work from anywhere. Additionally, as technologies advance, AI-driven business systems emerge, and the number of applications used across organizations continues to expand, IAM has become more complex, evolving into holistic approaches to identity management. These progressions include functionalities such as Identity Governance and Administration (IGA), Identity as a Service (IDaaS), and the focus of this article, Privileged Access Management (PAM).
So, what is Privileged Access Management (PAM)?
Core Security defines PAM as “a critical security control that enables organizations to simplify how they define, monitor, and manage privileged access across their IT systems, applications, and infrastructure.”
Because administrator accounts have greater privileges that allow them to access valuable data, it can be challenging to manage privileged accounts. PAM solutions centralize management of administrator profiles and ensure that the least privilege access is applied to give both human users and non-human identities only the access they need.
Of each of the three areas mentioned above, PAM is the most narrowly defined, but has significant responsibility for mitigating identity-related access risks as it pertains to privileged access. While IAM and IGA focus on wider levels of user access for resources, systems, and applications across the organization, PAM primarily defines and controls access for privileged users. In modern architectures, PAM is a foundational component of Zero Trust strategies and increasingly integrates with Identity Threat Detection and Response (ITDR) solutions for real-time monitoring of privileged activity.
What are privileged accounts?
Privileged accounts are often shared accounts that hold elevated access to data. More specifically, these accounts are the ones within your IT environment that hold the “keys to the kingdom.” Examples of elevated privileges include the ability to change system configuration, install or remove software, or add, remove or alter user accounts. Below are three types of privileged accounts:
- Root/Administrator Accounts: These accounts possess full authority to systems and have no restriction for accessing services or data residing on a server. They are considered the most valuable targets for threat actors.
- System Accounts: These accounts are used for running operating system services and can modify the relevant files and configurations. They are typically provisioned with the operating system.
- Service/Application Accounts: These accounts are used for running processes and applications through automated, often unattended tasks. They frequently own or have access to data, resources, or configurations not available to non-privileged users.
- Machine Learning/AI System Accounts: Identities that control access to AI models, training datasets, and automated decision-making processes, often with access to sensitive or proprietary information.
Additionally, privileged credentials can also take the form of API keys, certificates, and secrets that grant wide system or data access.
In order to successfully implement a PAM solution, each organization should determine what is classified as privileged data, where it lives, and who (whether human or non-human) can access it.
How can you as a security leader ensure the effectiveness of a PAM solution?
In order to successfully protect your organizations against unauthorized third-party user access, a strong security posture built around privileged access management (as well as IGA) is critical. Here are a few considerations to keep in mind when deciding on a PAM solution:
- Ease of Integration: Your PAM solution should be compatible with all types of applications, from on-premise to cloud apps, and support multi-cloud environments and containerized workloads. It must integrate and be interoperable with third-party solutions to maximize your security investments.
- Ease of Use: Your PAM solution will only be effective if it’s properly adopted. Difficulty and complexity in use risk the solution being ignored or circumvented. Choose a solution that ensures low friction for privileged users and non-human identities, and that can handle high-volume automated access requests without manual process delays.
- Ease of Implementation: Solutions failing to deliver anticipated benefits often happens because they were not fully implemented, so your chosen PAM solution should easily integrate with the existing technology stack, enable rapid roll-out, and include automated discovery of all privileged identities—human and non-human—across your environment.
For more information and to see how K logix can help you address your PAM challenges, contact one of our experts.