Updated on August 27, 2025
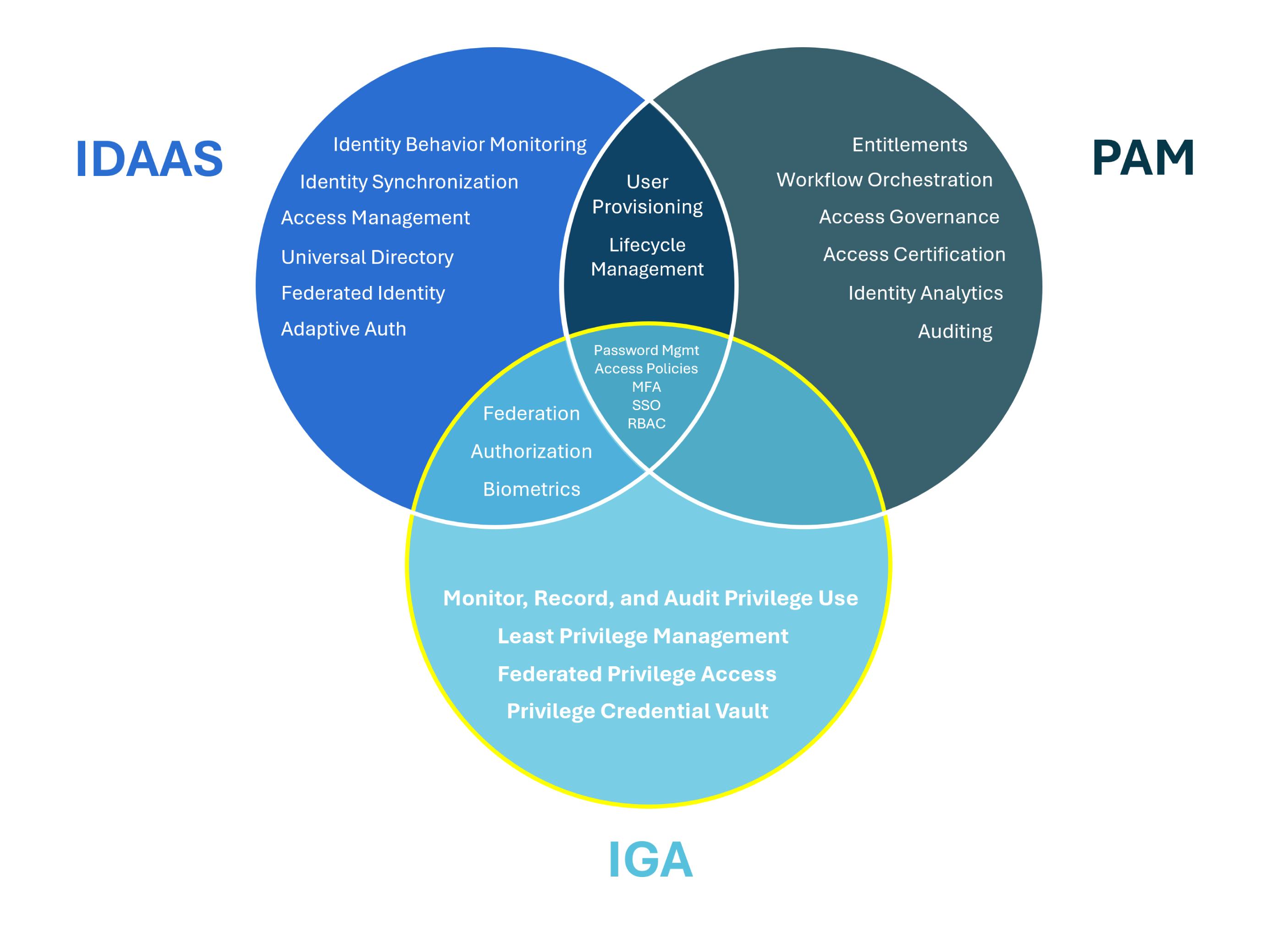
Identity and Access Management (IAM) has long answered the “how” behind granting and governing user access to resources “managing digital identities and user access to data, systems, and resources within an organization." IAM programs help to reduce access risks related specifically to identity. The importance of properly managing identities has become more significant in recent years, forcing organizations to consider new solutions that will minimize disruptions in user’s abilities to work. Furthermore, as technologies advance and the number of applications used across organizations expand, IAM has become more complex, evolving into holistic approaches to identity management. These progressions include programs such as Privileged Access Management (PAM), Identity as a Service (IDaaS), and the focus of this article, Identity Governance and Administration (IGA).
So, what is IGA? **
Core Security defines IGA “as both a policy framework and set of security solutions that enable organizations to more effectively mitigate identity-related access risks within their business.” Simply put, the IGA strategy allows for automation of credential provisioning, tracking, recertification, and removal. Additionally, IGA offers solutions for ease of password management, governance and compliance management, and risk management. While IAM mechanisms of the past have offered similar contributions by way of access management, IGA encompasses more than your run-of-the-mill IAM tool, including management of “third-party vendors and nonhuman identities such as applications into their business processes."
One of the most frequently asked questions by clients is: “What is my return on investment (ROI) for a technology like this?” The truth of the matter is that ROI is not immediately recognizable when technology solutions are implemented. Perhaps you’ve recently purchased an endpoint solution that has yet to recognize malicious activity on company-provisioned laptops. Does that mean the acquisition of this technology was moot? You tell us when that high priority alert comes through. As for IGA, “a modern IGA automates security access in a fast, efficient, consistent and accurate way – and at scale." While the initial cost for IGA is significant, “as the organization grows, IGA share in total costs gets reduced, while the role and importance are growing."
Is IGA the right solution for my organization?
This question, while subjective in nature, depends entirely upon each organization’s security focus. Per a study conducted by K logix in July of 2025, 57% of organizations listed IAM as one of their top investment areas. Organizations typically prioritize IGA when they face rapid SaaS adoption, multi-cloud entitlements, frequent workforce changes or M&A, significant third-party access, audit findings, growth in non-human identities, or long lead times for access changes. The best next step is an objective posture assessment and requirements exercise to pinpoint where IGA can deliver the most value.
How can you as a security leader ensure the effectiveness of an IGA solution?
“We are talking mostly about personnel management, including identity and access management. The 'maturity' of these processes directly affects the quality of the implementation of the IGA system." In other words, the success of IGA is dependent upon the existing information security structure. The K logix Research Team is equipped with security professionals who can assist with requirements gathering to identify a list of solutions catered to your organization’s needs. Through strong relationships with vendors across the industry, K logix is enabled to find you the best fit solution to assist with building a holistic, well-protected technology stack. K logix’s team of consultants are similarly available to conduct comprehensive reviews of your existing IDAM program, offering recommendations for enhancement to satisfy regulatory, internal, or legal requirements.
Identity Governance and Administration is one of the many advancements being made in the realm of cybersecurity. As automation reshapes how we manage access across SaaS and multi-cloud, organizations that modernize identity governance see stronger controls and smoother operations. It is essential that we look internally at our own security programs to understand where we can leverage these new tools to ensure strengthened security that offers proper protection for all users.
Read more about our Identity and Access Management Program Review.
For further information on how K logix can help you achieve your IDAM-related goals, contact one of our experts.