IAM in 2021: The New Security Perimeter
Published On: June 29, 2021
Identity and Access Management (IAM) is a strategic goal for many CISOs and security leaders, and the need for strong programs is more important than ever before. IAM is the anchor in the effort to make organizations robust, agile, and secure. However, there is an expressed confusion in the market when actually putting IAM programs in place, from processes to technology investment decision.
Before we dive into how IAM is expanding in 2021, let’s define what an IAM program is: simply put, IAM is a structure of business processes, policies, and technologies that “facilitates the management of electronic or digital identities.” With an IAM framework in place, security professionals may control user access to sensitive and important information inside their organizations.
IAM solutions can be deployed on premises, provided by a third-party vendor through a cloud-based model, or deployed via a hybrid model.
On a fundamental level, IAM is comprised of the following elements:
- How individuals are identified in a system
- How roles are identified in a system and how they are assigned to individuals;
- Adding, removing, and updating individuals and their roles in a system;
- Assigning levels of access to individuals or groups of individuals; and
- Protecting the sensitive data within the system and securing the system itself.
IAM Core Components
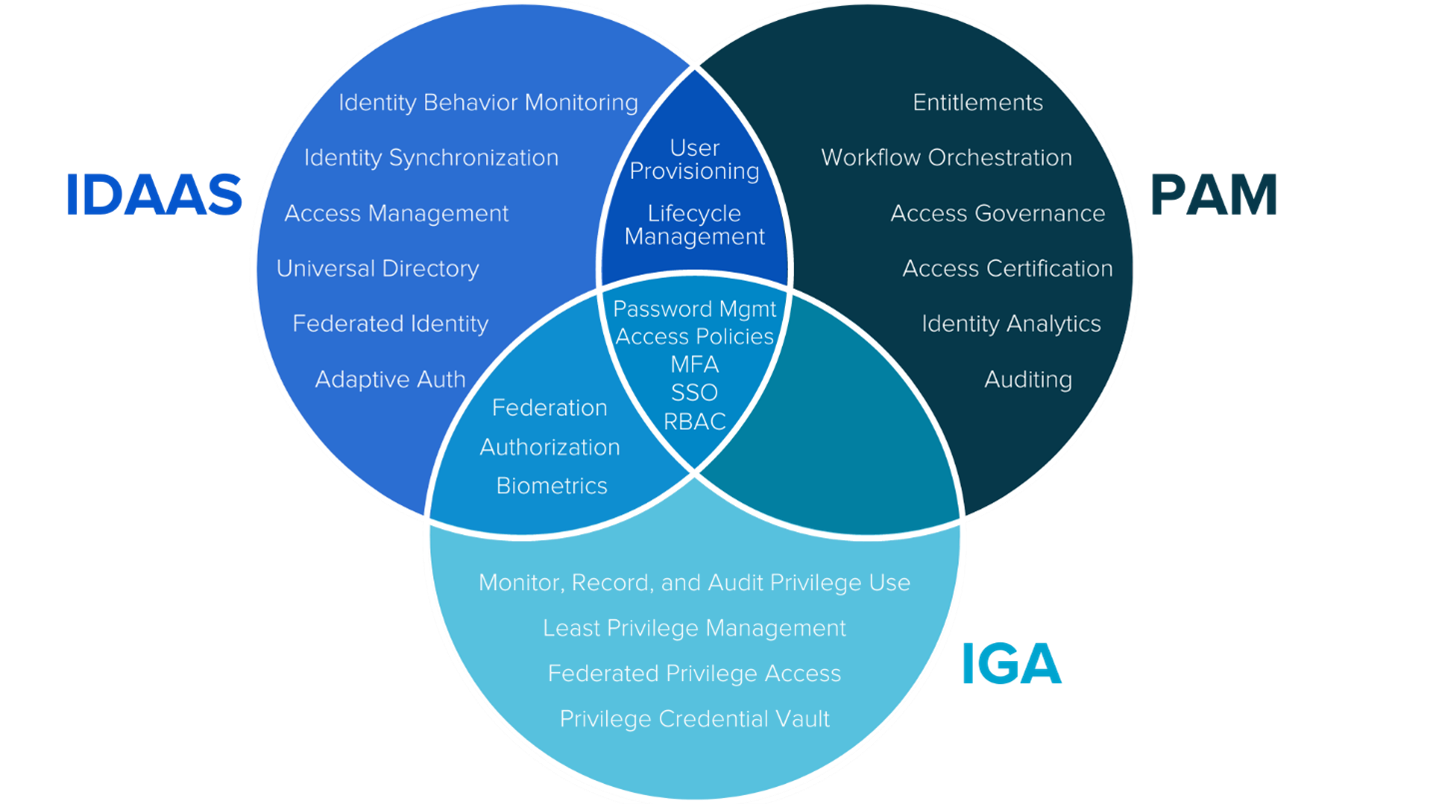
One of the top challenges around IAM is what elements organizations should invest in based on their specific technical and business requirements. Through K logix’s Research Department, our experts have identified the three most prominent areas of IAM as Identity as a Service (IDaaS), Identity Governance and Administration (IGA), and Privileged Access Management (PAM). We have defined them as:
- Identity as a Service (IDaaS): IDaaS products synchronize identities within a business and across that business’s relationships offering a single source of truth for identity management. These platforms also manage the depth of access, regulating not just who gets access but what is accessed and how.
- Identity Governance and Administration (IGA): IGA platforms are “tools designed to manage digital identity and entitlements (access rights) across multiple systems and applications." Sitting at the nexus of business and security objectives, IGA platforms contextualize and then map the relationship between identities, users, access, and data.
- Privilege Access Management (PAM): PAM solutions discover, monitor and regulate the creation, removal, storage and use of privileged credentials, facilitating visibility and control over privileged users, accounts, applications, and systems. By centralizing privileged environments, PAM solutions minimize the risk of credential theft and privilege misuse.
Since much of the language used to describe the three areas have some areas of similarity and overlap, we have created a Venn Diagram to showcase what constitutes each component.
The pandemic has increased the visibility of IAM and emphasized the obstacles ahead for leading security professionals.
According to K logix CISO research, these are the top challenges that security leaders will be addressing in 2021 and beyond:
- Third party customers, their suppliers, consultants, contractors, etc. accessing different pieces of an organization’s environment
- Collaboration between technologies to deliver robust IAM capabilities
- Managing the impact of digital transformation
- Driving IAM standardization and automation
Remote work is the new normal for many organizations, and having an IAM strategy in place will become paramount to remain secure. Prior to the pandemic, security teams relied on perimeter-based security models and leveraged firewalls to protect their company networks and employees from cyberthreats. However, as employees shifted to working remotely and began accessing applications through different devices in various locations, security leaders have focused on securing the identity of the user.
The old paradigm of a perimeter-based approach to security is being replaced by a new one, centered on the concept of Zero Trust with identity at its core.
In a cloud-native world, identity is the new security perimeter. As the Zero Trust model becomes more widely adopted, security professionals are implementing IAM controls that grant users access to the network from anywhere while still maintaining centralized security. Zero Trust assumes that no one is trusted. Based on our research through Feats of Strength magazine, 9 out of 10 CISOs we spoke with said Zero Trust is a process, not a technology, and truly comes down to how access is granted.
A core component of Zero Trust is the identity of the user and/or asset. When it comes to implementing this model, you can have all the security controls in place, but they won’t effectively secure your organization unless you know who your user is and what they have access to. Namely, you can’t solve for Zero Trust without solving for identity first.
With identity as the perimeter, implementing a Zero Trust model solves the challenges associated with digital transformation and the growing remote workforce. While the idea is straightforward, its simplicity is deceptive; there is no single technology to help organizations achieve Zero Trust. As Kathy Hughes states on page 5 of the September 2020 issue of Feats of strength, "Zero Trust is a process, approach and methodology - not a product or technology solution." This model is not a one size fits all solution and cannot be implemented by purchasing a single product. As your organization moves through its zero trust efforts, identity must be at the core of its adoption.
Enterprises that develop mature IAM capabilities may reduce their identity management costs and become more agile in supporting new business initiatives.
IAM addresses the need to ensure appropriate access to resources across increasingly heterogeneous technology environments, and to meet rigorous compliance requirements. A crucial undertaking for any enterprise, IAM is increasingly business-aligned, and requires business skills, not just technical expertise.
Maintaining the flow of business data while simultaneously managing access has always been a top challenge for security programs. The cybersecurity environment is ever-evolving, and the difficulties have only become greater with trends such as bring-your-own-device (BYOD), cloud computing, mobile apps, and the increasingly mobile workforce. There are more devices and services to be managed than ever before, with diverse requirements for access privilege. An IAM program must be business-aligned to ensure the organization protects sensitive information and moves at the same pace as digital transformation.
The push towards digital transformation is bringing IAM to the forefront of CISO priorities and driving investment in IAM strategy and technology.
In 2021, organizations will continue to adopt technologies that service IAM priorities as they look to give employees a secure way to connect to devices, networks, and applications while simultaneously advancing the goals and needs of the business. This focus on security will become even more prevalent as organizations establish strong remote security cultures. Whether through new products or training, cybersecurity leaders are placing a stronger security focus into their employees' everyday lives in the most frictionless ways possible.
How K logix can help navigate the IAM space
Regardless of your IAM program maturity, K logix meets customers where they are and offers services around:
- IAM strategy: Unify your identity technology and program strategy with formally documented resources and justification.
- IAM technology decision: Understand the IAM technology marketspace and which technology (or technologies) are the best fit based on your specific requirements. Leverage K logix’s agnostic analysis informed by quantitative scoring and budget requirements.
Contact us for more information on how we can work together to strengthen your IAM program.
Subscribe
Stay up to date with cyber security trends and more

