
Trust is a vulnerability. That is the chief motto of a Zero Trust security model, with the goal of eliminating any unauthorized access to data and services. And yet, its simplicity is deceptive; there is no single technology or method to help organizations achieve Zero Trust (Forrester, 2015).
Zero Trust challenges the traditional, perimeter-based “castle and moat” security model by changing the “perimeter” to anywhere within an organization where access control decisions occur (Nather, 2020). With a “castle and moat” security model, hackers do not meet much resistance moving inside internal systems. But, by following Zero Trust principles, security is ubiquitous within an organization as its users, devices and applications need to regularly re-establish trust to an organization’s assets.
Security professionals have been moving away from the “castle and moat” model for a while now. So, why then, is Zero Trust such a pervasive term in security circles today? John Kindervag, when inventing the term in 2010, identified three core Zero Trust principles: 1) verify and secure all resources, 2) limit and strictly enforce access control, and 3) inspect and log all traffic (Forrester, 2010). These principles have encouraged and guided security professionals to build bottom-up approaches for implementing a Zero Trust architecture. Notable models include ones published by Google and NIST (Google, 2014; NIST, 2020). The security market also offers better tech to implement Zero Trust, further explaining its current fame (Nather, 2020).
Zero Trust gets a bad rap in some circles because many models for implementation assume systems are being built from scratch, as is the case in Google’s notorious Zero Trust initiative, BeyondCorp. Google wanted to give employees the ability to work remotely from an untrusted network without requiring the use of a VPN. In doing so, over the course of eight years, Google reinvented its network architecture by 1) identifying the applications, services and infrastructures subject to access control and assigning those entry points a minimum trust tier, 2) allowing only managed devices to access corporate applications via a device inventory database, 3) securely identifying users via a user and group database, and SSO, 4) creating an unprivileged network, 5) externalizing applications and workflows, and 6) implementing inventory-based access control. Just reading the steps Google took will leave a person winded, so needless to say, it’s not an achievable model for most organizations.
But Zero Trust does not have to be radical. Many security professionals believe it has incremental value and the NIST Zero Trust report recommends organizations seek to incrementally implement Zero Trust principles. The NIST report recognizes that organizations will likely operate in a hybrid Zero Trust/perimeter-based model for an indefinite period, but suggests organizations begin investing in Zero Trust initiatives today (NIST, 2020).
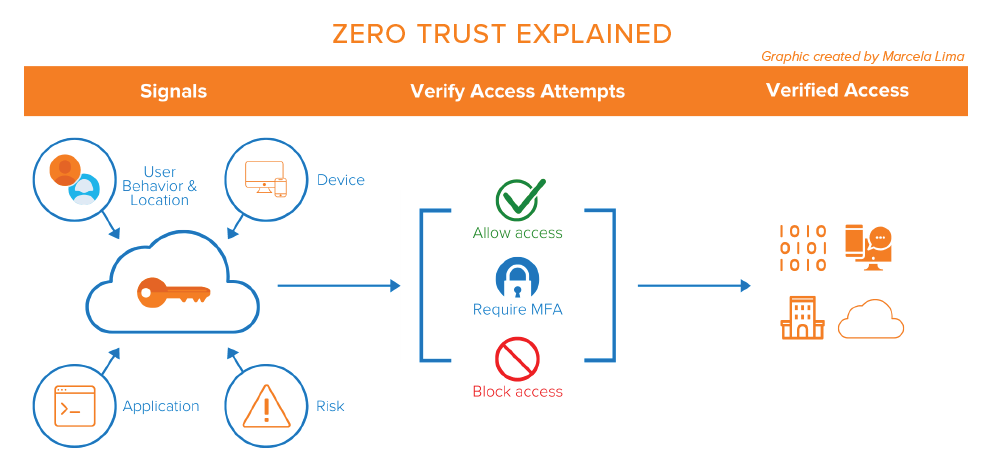
While there is no single approach to Zero Trust security, here are some useful steps, distilled from an assortment of sources, to guide an organization along its journey: 1) Identify the organization’s protect surface - what is its network’s most critical and valuable data, assets, applications and services?; 2) Gain visibility into the organization’s network’s activity and current solutions - how does traffic move within the organization in relation to the protect surface?; 3) Map the flow of the organization’s sensitive data – does the organization have an up-to-date asset inventory?; 4) Create micro-networks and implement access control, and finally 5) Continuously monitor and authenticate (Forrester, 2015; Nather, 2020; NIST, 2020; Palo Alto Networks, 2018).
Works Cited
Forrester, 2015. Case Study: Westjet Redefines Its Security With Forrester’s Zero Trust Model. Forrester.
Forrester, 2010. No More Chewy Centers: Introducing The Zero Trust Model Of Information Security. Forrester.
Google, 2014. Beyondcorp, An Overview: “A New Approach To Enterprise Security”. Google.
Nather, W., 2020. Getting Real: Sorting What’S ZT And What’S Just BS. [online] Brighttalk.com. Available at: <https://www.brighttalk.com/webcast/10415/383057/getting-real-sorting-what-s-zt-and-what-s-just-bs>.
NIST, 2020. Zero Trust Architecture. NIST.
Palo Alto Networks, 2018. What Is Zero Trust?. Palo Alto Network
Sydney's article was featured in the September 2020 issue of Feats of Strength, read the magazine issue here.