breaking down the wannacry attack & understanding how to prevent ransomware
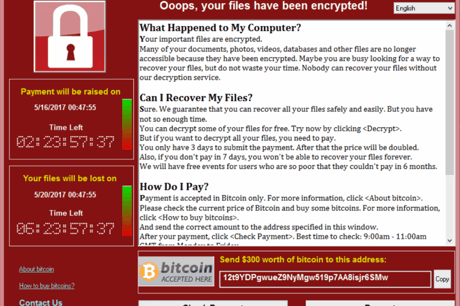
Last Friday, a worldwide WannaCry ransomware attack impacted more than 150 countries and major organizations across the globe. Currently, Europe officials report over 200,000 computers have been affected, with additional fallout expected. One of the biggest impacts has been on hospital and healthcare facilities, whose operations were severely disrupted by the attack.
WannaCry is an ongoing cyberattack of a ransomware computer worm targeting the Microsoft Windows operating system. It is suspected the attack arrived by phishing emails and once installed it uses a backdoor exploit developed by the U.S. National Security Agency to spread through local networks and remote hosts which lack recent security updates. All exposed systems are directly infected. While a critical patch was released by Microsoft on March 14, 2017 to remove the vulnerability, many organizations had not yet applied it.
How to Prevent Ransomware?
A proactive and fundamental information security posture is key. Prevention of all ransomware at all times in all of your business environments is a tall order. If an attack does occur, organizations must implement processes and technologies to ensure quick detection and response in order to contain harmful attacks. Here is a 6-step reminder check list:
- Perform Data Backup and Recovery.
Identify critical systems and data in your environment, including cloud environments, and continuously back up them regularly and securely. Ensure appropriate access to all company owned data that is being backed up. Testing your backup and recovery procedures regularly should be a part of the overall IT and Info Sec programs.
- Vulnerability and Patch Management.
Install recommended computer updates on a regular basis, including Microsoft Windows updates. Info Sec and IT should partner with eachother and find the most effective and quickest way to patch vulnerable systems in the environment.
- Audit Identity and Data Use.
Monitoring unusual or unauthorized changes to systems, user accounts, and files helps to detect indicators of ransomware activity so you may respond quickly and minimize negative impact. Integration of such tools and processes into your environment can take actions like disabling user accounts.
- Deploy Advanced Device Controls for Company Servers, Workstations, Laptops, Tablets, Phones, etc.
Next generation endpoint security and file integrity monitoring are essentials tools. The benefits of these types of tools are to detect and prevent malicious activity before ransomware actions are carried out.
- Implement the Least Privilege Principal and MFA.
Perform these for all user accounts across your environments wherever possible. Identity provisioning/de-provisioning, strong authentication, access rights, and application whitelisting are all aspects of this principal that are considered. Ransomware is typically attaching to user identities in order to gain access to files and encrypt data. Protect your data by protecting your identities.
- User Security Awareness.
Not only do security teams need to ensure they have taken the necessary steps to protect their organization’s systems and information, but there should always be a strong emphasis on training all employees and even contractors/third-parties that handle company information. This awareness must include education around social engineering and email phishing, so employees understand how to recognize potentially harmful web links or attachments. This is somethingwe believe should be tested and measured on as part of your ongoing program efforts.
Want to learn more about preventing ransomware? Reach out to our experts info@klogixsecurity.com.