Using Password Data to Elevate Penetration Testing
Published On: September 29, 2022
One of the first things that comes to mind on the topic of security are passwords. We use passwords every day to access resources and accounts through authentication. Attackers also love passwords, especially weak ones, as they are great targets for initial access and moving within an environment.
From an offensive perspective, compromising passwords are a good way to gain access to resources held behind authentication boundaries, whether this is the ability to further gain reconnaissance information and fingerprint devices, or the ability to move vertically and gain additional permissions. This makes plaintext password usage in environments rare and not recommended by security practices. Instead, authentication credentials are often passed and stored as hashes.
In their simplest form, hashes are the result of a one-way algorithm that transforms plaintext into a hash digest. This is different than encryption methods where decryption is intended; this means hashes cannot be decrypted. The most effective way of obtaining plaintext from a hash is to create another hash with a known plaintext and attempt to collide cipher text with the target hash. If the cipher text matches, then you know the password’s plaintext must also be the same.

Offensive security practitioners often use real password data as the gold standard when doing password attacks, as using passwords users have set are likely candidates. This makes collecting password breach data valuable as a data resource for analyzing how users construct or choose passwords and examining trends within password composition.
For example, if an environment enforces a password policy you might find the average users password composition different than an environment without one. Using this password metadata is a recommended part of password cracking methodologies and is incorporated into various password cracking toolkits.
Passwords for Active Directory might be considered weak even though they are required to have eight or more characters comprised of alphabetic, numeric and special characters. Examples of this would be an easily guessable password such as:

At K logix, we not only collect breached password data to identify these user trends, but we are also focused on improving overall password security for organizations. We take the reincorporation of data one step further by utilizing it with data analysis methods to better guess how users are setting passwords and what formats they are setting their passwords in. This allows us to elevate our service offerings and more aggressively target organizations that may be falling prey to weak password trends.
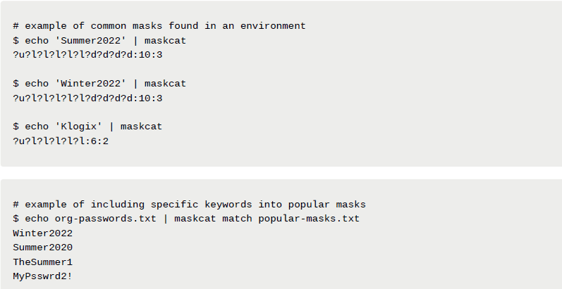
Our database compromises over 1,000,000,000+ passwords (1+ billion), spread throughout data breaches and data from real organizations filtered for low quality candidates. One of the first things in our analysis is to separate passwords by complexity and length to simulate our target environment more accurately. To do so, we use two tools created by our testing team, PwdStat and maskcat to better divide the data sample:

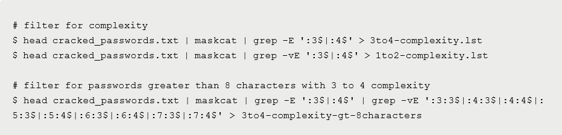
Both of these tools have the ability to further provide metadata about the plaintext values we use to filter down our targets to the most likely candidates. For example, if we are able to inspect the password policy of an Active Directory domain and the minimum password requirement is nine characters, then it would make sense to look for candidates and rules that conform to the policy. We can also use maskcat to do this by filtering down wordlists based on password masks (password structure) or identifying the most common password masks of the found passwords then trying additional candidates similar to them.
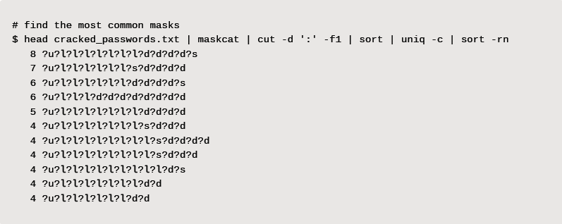
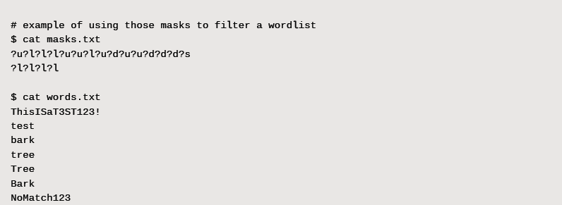
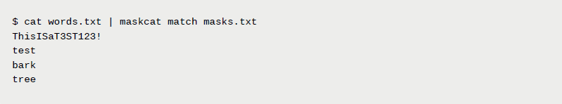
Password masks are very valuable when cracking passwords, as users tend to follow the same trends. For instance, if the password policy requires a special character and number, it is far more likely those will be found at the end of the password than at the start. Masks can also be useful for identifying machine generated passwords that follow a similar structure to increase the odds of cracking one.
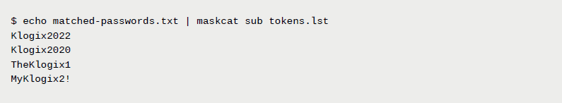
It is also recommended to capture unique tokens or words that may be used across many accounts that is specific to the organization such as the company name, product name, location, usernames, and naming conventions. Often, when creating passwords for services or users, this specific metadata will show up causing issues where base words might be shared across many accounts and services leading to rapid compromise when identified.
We can elevate both of these tricks by combining them into a single workflow with maskcat by submitting common tokens into common password masks. This way we target the most common password masks set by users and meet the password policy requirement. In addition, we target specific organizational keywords that may appear within hashed secrets simultaneously:
K LOGIX TIPS FOR ELEVATING PASSWORD SECURITY
So, how can defenders use this information to help better protect environments? We have some general recommendations for those who are interested in elevating their password security:
-
Review existing password policy for areas of improvement. This could be in the form of increasing complexity requirement, minimum length, or other factors that could be low hanging fruit.
-
Note about Password Expiration and Rotation: This is a common item we receive questions on. While enforcing some form of rotation will benefit the environment, causing too frequent password rotations could lead users to setting weaker and easier to guess passwords. Therefore, it is recommended to include some form of rotation but to work with the end users to best meet security requirements.
-
-
Consider implementing a process to verify if passwords set by users are known to be compromised in a data breach. These passwords are often attackers first choice when targeting hashes and can be quickly compromised.
-
Additional security guidance and controls are also provided by NIST and OWASP:
-
OWASP Application Security Verification Standard 2.1.7
-
NIST 5.1.1.2
-
-
-
Consider reviewing set passwords for easily guessable metadata, such as company name, product name, location, usernames, and naming conventions. Ensure that these candidates are also reviewed in mixed cases, leetspeak, and other common mutations attackers may try. Systemic password usage can lead to rapid compromise when shared material is used for secrets.
-
Consider reviewing set passwords for easily guessable password masks that attackers will use to attempt to enumerate passwords that follow common human patterns.
Need further recommendations? Please consider following K logix’s social media accounts as well as reach out to our talented team for further tips and tricks related to offensive security.
In the next hash cracking blog post, we will examine some tools specially crafted by our testing team to help store and aggregate password data so that security teams can utilize their offensive security password data more effectively.
References:
https://github.com/JakeWnuk/PwdStat
https://github.com/JakeWnuk/maskcat
https://github.com/JakeWnuk/PwdStat
https://owasp.org/www-pdf-archive/OWASP_Application_Security_Verification_Standard_4.0-en.pdf
https://pages.nist.gov/800-63-3/sp800-63b.html#sec5
Subscribe
Stay up to date with cyber security trends and more


