We speak with CISOs on a regular basis about their challenges and their need to gain a clear picture into their entire security program. They want to understand prioritized action items for improvement, and for their security programs to make a positive impact on the business and create a competitive advantage.
Many CISOs complete risk assessments, however the majority tell us they are compliance-driven, done internally, and/or lack key directives to advance their program. We listened to these needs in the marketspace and recognized many risk assessments lacked executive-friendly results and failed to include specific, prioritized action items.
In response, K logix established an Actionable Risk Assessment (ARA) service, spearheaded by Erin Benson, our Security Practice Director.
In the following Q&A, Erin answers questions about ARA’s impact on security leadership and business executives. If you’d like to learn more, don’t hesitate to let us know; info@klogixsecurity.com.
Q: What do traditional risk assessments lack?
Erin: I worked for 10+ years in the traditional IT audit space and completed more than 100 risk assessments. What I found was companies often take a prioritized list of findings from the audit and attempt to take a “divide and conquer” approach to remediate findings. The problem with this approach is it lacks top-level strategic planning, which results in redundant efforts and a focus on the surface-level symptoms instead of underlying root causes. Successful advancement of enterprise-wide security posture demands a strategic approach to planning and sequencing of security initiatives.
Furthermore, traditional risk assessments are often done internally, which can lead to a host of problems. First, while an internal assessor may have a handle on their current security program, they sometimes lack knowledge or perspective on how it can be advanced, strengthened, or improved. Second, internal staff may be reluctant to assign blame to their coworkers (or themselves!) for problems they uncover. Finally, there is a common misperception that risk assessments create an incremental quantity of “extra work” for the security team. The reality is risk assessments often uncover time-consuming manual processes and identify opportunities for automation, integration, and efficiency. Risk assessments may “unburden” the security team by highlighting the “roots” of security problems. Vendor management, cross-functional project management and enterprise risk management – oftentimes remediation of critical security risks requires these functions to “step-up” their protocols.
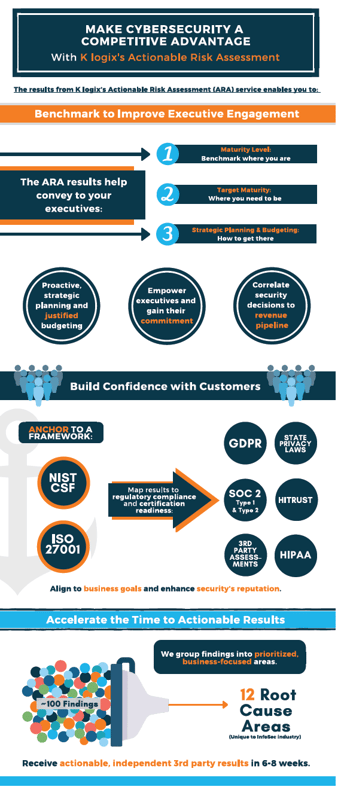
Q: How does ARA provide a basis of alignment for security programs?
Erin: To start, ARA results are tailored specifically for the customer’s executive teams and budget decision makers. Then we anchor our findings to the framework of their choice, whether it’s NIST or ISO. We also have the ability to take previously produced findings from NIST or other assessments and plug them into our ARA methodology.
The results are grouped into twelve common ‘root cause’ areas, which means security teams won’t have to sift through (and try to make sense of) a long list of findings. Additionally, the findings are mapped according to a customer’s relevant regulatory and certification targets, such as GDPR, State Privacy Laws, HIPAA, SOC 2, and more. Finally, we provide a roadmap that concisely lays out the progress of remediation efforts, target areas, and business-focused action plans.
Q: What makes ARA results business-focused?
Erin: Simply put, ARA builds trust by clearly showing where a company’s security program stands, where it needs to be, and how to get there. Importantly, our findings are based on a maturity scale that is gauged relative to similarly sized businesses in our customer’s industry. This gives security leaders a simple tool for justifying budget and gives executives the ability to measure progress over time.
Q: What deliverables does ARA provide?
Erin: An effective risk assessment should provide two things: executive engagement via a compelling high-level summary and security team guidance via specific risk-mitigation recommendations. K logix’s ARA does just that with a clear and concise matrix, narrative report, and business-friendly presentation. The matrix includes control-level findings and detailed recommendations for closing gaps and the narrative report supplements this information with strong reasoning and details behind the maturity scores and results. Together with the business-friendly presentation, ARA helps security leaders make compelling, quantifiable business-cases to budget decision makers to enable ongoing security program advancement.