.png?width=2000&name=In%202021%20graphic%20(1).png)
PROGRAM FIRST, TECHNOLOGY SECOND
Having a solid approach and defense against insider threat starts with implementing a strong, strategic program. Many times, security leaders jump to investing in a new technology to address insider threat, without an adequate program in place. This may result in insufficient protection and an ad hoc approach without considerations for business requirements.
On page 8, Patty Ryan (CISO, Ortho Clinical Diagnostics) explains, “I think the biggest issue with insider threat is the transparency or lack of transparency. Once you have the transparency, in my opinion, you can start building the rules and a logic that allows you to understand abnormal from normal. It is not easy and is a multi-layered approach.”
The risk around insider threat is rising as corporate environments increase in complexity. On page 10, John Mandracchia, CISO at Health Plans, Inc. says it does not take a technically minded individual to penetrate an organization and become an internal threat in today’s world.
IN 2021 AND BEYOND, INSIDER THREATS ARE A FOCUS ARE DUE TO:
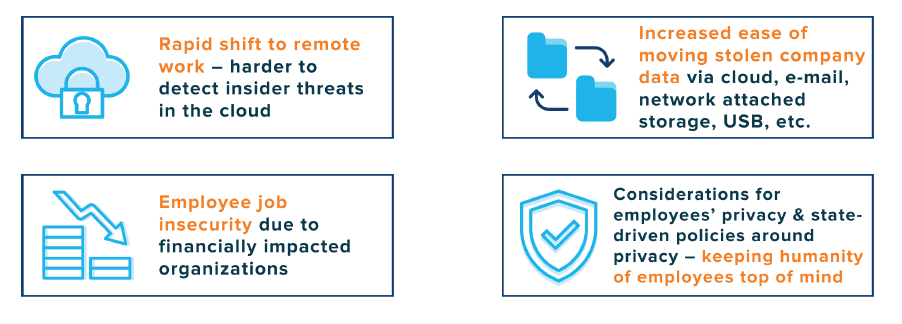
THE PANDEMIC’S IMPACT ON INSIDER THREAT
An increasing number of remote workforces, accelerated cloud migrations and even recent breaches such as SolarWinds have added layers of complexity to insider threat as many organizations are losing varying levels of visibility and control.
On page 6, Andrew Smeaton (Global CISO, DataRobot) says – “Remote work, during this pandemic, has opened up new insider threats. Many people have lost their jobs, and some are scared of losing. As a result, users might download their work files to an unsecured computer for future reference, which increases security risks. Furthermore, remote employees might use their personal laptops and computers not protected by the organizations’ security bubble, such as web gateways, intrusion detection systems, firewalls, endpoint protection systems, etc. This significantly increases the risk of data theft.”
INSIDER THREAT IMPACT
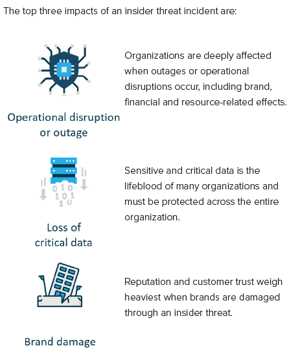
Other impacts may include legal liabilities, loss in competitive edge, or loss in revenue.
EFFECTIVE INSIDER THREAT PROGRAMS
According to CISA**, successful insider threat mitigation programs employ practices and systems that limit or monitor access across organizational functions. Those practices and systems, in turn, limit the amount of damage an insider can do, whether the act is intentional or unintentional.
In every case, effective insider threat mitigation programs need to be able to detect and identify improper or illegal actions, assess threats to determine levels of risk, and implement solutions to manage and mitigate the potential consequences of an insider incident (CISA).
Many organizations may view insider threat programs as costly and resource-exhaustive, due to considerations such as legal and privacy concerns. However, security leaders must ensure they leverage existing skillsets within their teams and evaluate or operationalize any technology that may add insider threat coverage. They must also clearly articulate to business leaders the impact of an insider threat and justify the resources required to build and maintain a robust program.
According to CISA, effective insider threat programs:

Sources:
*Cybersecurity Insiders. “2020 Insider Threat Report.” https://www.cybersecurity-insiders.com/wp-content/uploads/2019/11/2020-Insider-Threat-Report-Gurucul.pdf
**Cybersecurity and Infrastructure Security Agency. “Insider Threat Mitigation Guide.” November 2020. https://www.cisa.gov/sites/default/files/publications/Insider%20Threat%20Mitigation%20Guide_Final_508.pdf