Identity and Access Management (IAM) is a strategic goal for many CISOs and security leaders, and the need for strong programs is more important than ever before. The approach, program strategy, and technology investments around IAM vary based on an organization’s specific requirements.
IAM is a structure of business processes, policies, and technologies that facilitates the management of identities. With an IAM framework and program in place, security professionals may control user access to sensitive and important information inside their organizations.
IAM CORE COMPONENTS
One of the top challenges around IAM is peeling back the layers and understanding what types of IAM technology to invest in based on an organization’s specific requirements, technologies they already have in place, implemented processes, among many other nuances. Through K logix’s Research Department, our experts have identified the three most prominent areas of IAM as: Identity as a Service (IDaaS), Identity Governance and Administration (IGA), and Privileged Access Management (PAM). We have defined them as:
IDENTITY AS A SERVICE (IDAAS)
IDaaS products synchronize identities within a business and across that business’s relationships offering a single source of truth for identity management. These platforms also manage the depth of access, regulating not just who gets access but what is accessed and how.
IDENTITY GOVERNANCE AND ADMINISTRATION (IGA)
IGA platforms are “tools designed to manage digital identity and entitlements (access rights) across multiple systems and applications” (Gartner). Sitting at the nexus of business and security objectives, IGA platforms contextualize and then map the relationship between identities, users, access, and data.
PRIVILEGE ACCESS MANAGEMENT (PAM)
PAM solutions discover, monitor and regulate the creation, removal, storage and use of privileged credentials, facilitating visibility and control over privileged users, accounts, applications and systems. By centralizing privileged environments, PAM solutions minimize the risk of credential theft and privilege misuse.
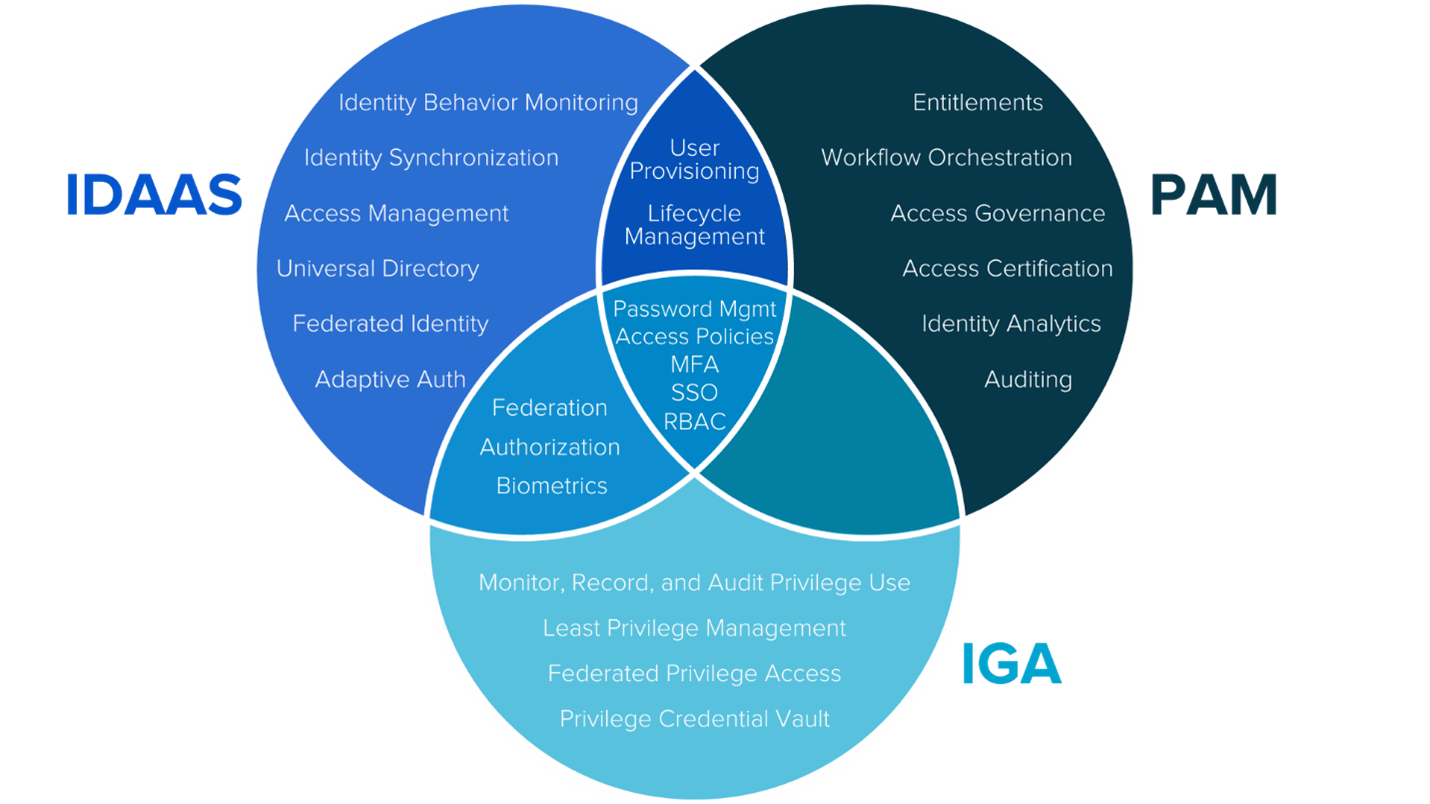
Since much of the language used to describe the three areas have some areas of similarity and overlap, we have created a Venn Diagram to showcase these areas.
IAM CHALLENGES
According to K logix CISO research, these are the top IAM challenges security leaders will be addressing in 2021 and beyond:
- Collaboration between technologies to deliver robust IAM capabilities
- Managing the impact of digital transformation
- Driving IAM standardization and automation
- Third party customers, their suppliers, consultants, contractors, etc. accessing different pieces of an organization’s environment
A strong IAM strategy in place is paramount for organizations to address the transformative landscape of businesses. In a cloud-native world, identity is the new security perimeter. As the Zero Trust model becomes more widely adopted, security professionals are implementing IAM controls that grant users access to the network from anywhere while still maintaining centralized security.
IAM addresses the need to ensure appropriate access to resources across increasingly heterogeneous technology environments, and to meet rigorous compliance requirements. A crucial undertaking for any enterprise, IAM is increasingly business-aligned, and requires business skills, not just technical expertise.
Keeping the flow of business data while simultaneously managing access has always been a top challenge for security programs. The cybersecurity environment is ever-evolving, and the difficulties have only become greater with recent trends such as bring-your-own-device (BYOD), cloud computing, mobile apps, and remote workforces. There are more devices and services to be managed than ever before, with diverse requirements for access privilege. An IAM program must be business-aligned to ensure the organization can protect its sensitive information and allow it to move with the pace of digital transformation.
If you are interested in learning more about K logix’s agnostic IAM research, please reach out to us.