Cloud Native Application Protection Platform (CNAPP) is “an integrated set of security and compliance capabilities designed to help secure and protect cloud-native applications across development and production (Gartner).” The term was coined by Gartner, who recognized the expanding needs that go into securing applications in the cloud. Broadly speaking, CNAPP solutions aim to address workload and configuration security by scanning applications in development and protecting them at runtime.
CNAPP is a culmination of the market shifts from raw virtualization of workloads going back two decades, to automating security of both the workloads and the environments in which those workloads run. The purpose of CNAPP is to unify and orchestrate independent solutions or architectures to enforce application behaviors that conform to the developer’s intent.
CNAPP is a combination of “Cloud-Native”:
Security tools (e.g.; code analysis, posture management and workload protections)
Data sources (logs and telemetry)
Automated coding practices (Continuous Integration/Continuous Delivery, aka “CI/CD”)
CNAPP serves as a convergence of multiple technologies, combining the capabilities of existing cloud security solutions, primarily Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platforms (CWPP), Cloud Infrastructure Entitlement Management (CIEM), Kubernetes Security Posture Management (KSPM), API protection, serverless security (microservices), code repository integration (e.g.; GitHub, BitBucket, etc.) and more.
Cloud-native applications are built on a foundation of containerization and microservices. This architecture enables the CNAPP to protect the application throughout its lifecycle. CNAPPs enforce the developer’s intent by enforcing secure coding practices (e.g., ban hard-coded secrets) and integrates those with approved container configurations at application runtime.
The environment in which cloud-native applications run is defined using “Infrastructure as Code” (aka. “IaC” such as Terraform, Ansible, etc). If the runtime configuration of the application should “drift” from that which was approved when the code was promoted to production, a CNAPP can block or report this activity for remediation. Key to this functionality is a technique known as “IaC scanning”, which is integrated into the CI/CD pipeline.
CNAPP AND SHIFTING LEFT
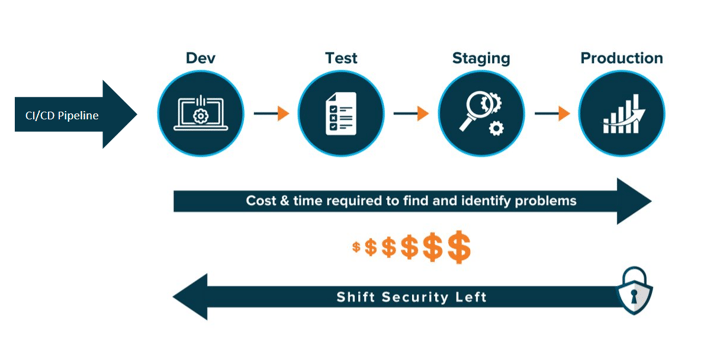
Developing cloud-native applications with security baked-in is another way of saying “shift-left” application security. Shifting security left means implementing security measures from the beginning of, and during the development lifecycle, rather than at the end of the cycle. CNAPPs work with the shift-left mentality by integrating secure coding techniques within the CI/CD pipeline. CNAPP platforms scan the CI/CD pipeline to look for coding errors, as well as to enforce the environmental controls on the application at runtime.
The benefit of shifting security left is identifying security issues before they cause damage or become too costly to remediate.
WHY DO CNAPPs EXIST?
There are two important elements in the term CNAPP that help explain why it exists. The first is “cloud-native.” The shift to the cloud has brought a wide range of new security needs along with it. The rise of dynamic and ephemeral environments within the cloud have increased complexity and created unique and unpredictable interactions. Traditional agent-based security approaches are not able to provide the appropriate coverage required to keep up with ephemeral, containerized, and serverless environments.
The second element is “application protection.” Previously, most cloud security tooling was focused on helping teams understand the security of their infrastructure. However, as Gartner says, “it’s no longer enough to ask, ‘Is my cloud infrastructure secure?’ Security tools must now ask, ‘Are my cloud applications secure?’”
When it comes to cloud applications, organizations need to be holistic in their security thinking. There are many ways to expose applications to risk in the cloud, from unintentional public internet exposure to overly permissive access rights, and more. Organizations should focus on identifying and mitigating the highest priority risks their cloud applications are exposed to, not just collecting a long list of security-related issues that in isolation pose little risk. With individual point solutions, they often narrowly focus on a limited set of security issues and do not integrate well together when it comes to correlating their signals, leading to challenges around prioritizing many low-priority alerts.
KEY COMPONENTS OF CNAPP
As CNAPP represents a convergence of existing security product categories, let’s briefly review what capabilities fall under the CNAPP umbrella. Everything below represents an existing point solution. CNAPPs bring aspects of these point solutions together to provide full stack visibility across cloud environments and shift the focus from individual security issues to broader, interconnected combinations of issues that pose a critical risk.
CSPM
CSPM solutions are focused on identifying misconfigurations in cloud resources and tracking compliance to different controls and frameworks. They focus on the cloud control plane, examining cloud infrastructure at the provider level. CNAPPs perform a deeper analysis of configurations and combine them with other inputs to identify and prioritize actual risks.
CWPP
CWPP is about securing cloud workloads, such as VMs, containers, and serverless functions, regardless of their location. CWPP capabilities go inside the workload, scanning for vulnerabilities, workload configurations, hard-coded secrets, API keys, and more. CNAPPs leverage CWPP capabilities to identify issues in the data plane within the workloads themselves.
Supporting tooling: CIEM, KSPM, serverless, and more.
While CSPM and CWPP capabilities are the primary components of CNAPP, a complete CNAPP solution will bring in elements of other cloud security tooling. Some examples include:
CIEM
CIEMs deliver infrastructure entitlement management capabilities so organizations can enforce related governance controls. Identity and access governance represent an important risk area that CNAPPs should be able to address. For example, Wiz recently found that 82% of cloud companies unknowingly gave 3rd party providers access to all their cloud data.
KSPM
KSPMs are a special type of CWPP. Containers such as Kubernetes are essentially workloads that run workloads. KSPMs are essentially CSPMs for Kubernetes. They focus on Kubernetes-related misconfigurations and security needs. For CNAPPs, bringing in a dedicated focus on Kubernetes and container security is important for cloud-native environments.
If you are interested in learning more about CNAPP, K logix has extensive educational workshops. Don’t hesitate to reach out to us.