CISO Quickfire Q&A
Published On: June 4, 2018


- During the RSA conference, we asked leading CISOs their thoughts on current trends, and in this article reveal their answers.
Throughout quickfire 30 minute interviews, we asked each CISO the same questions and compiled them to provide insight into current CISO challenges, approaches, and strategies. The topics we asked included:- - Digital transformation
- - Clearing the security product clutter
- - GDPR
- - CISOs top strategic goals
- - 3rd party assessments
- - RSA conference trends
- - Metrics and benchmarking
- All of the statistics, polls, and content you read in the next few pages are directly from the CISO interviews we conducted over the course of the conference.
The first question we asked CISOs was - what words would you use to describe your own information security program?
- The top words used by CISOs were enablement, protect and respond, and trust.
ENABLEMENT. CISOs who value enabling the business are working hard to align with, and educate, executives in order to embed this approach in the organization’s culture. These strong cybersecurity programs fuel innovation by encouraging the expansion of digital offerings and business strategies.
Furthermore, it means allowing the organization to function and operate as a revenue generating, innovative organization without security being perceived as a negative impact. It is all about enabling business strategies so CISOs can encourage innovation as organizations grow, without the implications of security challenging the ability to do so.
PROTECT AND RESPOND. Not only do CISOs want to fully enable the business, but they want to ensure they are protecting and responding at the same time.
“We are here to protect the digital assets of the company and to respond appropriately when there is something averse happening to us. Every good CISO is a good risk manager and not necessarily a technologist. They must understand their business and the risks their products and services face. From a cyber perspective, they build an investment portfolio around protecting and mitigating those risks in the long-term,” says Mike Raeder, CISO of OrbitalATK.
TRUST. There are different types of trust that CISOs strive for, including customer trust, executive trust, and team trust. One core component of a CISO’s program is ensuring security is baked into all facets of the organization and to ensure customer data is safe and protected. In many organizations today, organizations are transparent with customers about the level of security in their services or products, encouraging trust.
On describing his security program, Rich Licato, CISO of ARC comments, “I would say trusted, secure and culturally aware. What are you doing for security awareness? Cybersecurity is not a department, but an attitude. It must be ingrained within the culture for it to be effective. That’s probably the toughest thing for a CISO to establish because culture is so hard to change and it’s about trying to find the ways to change that conversation in order to change the culture and get everybody on the same page.”
Other CISOs have cohesive missions they use to describe their programs. Christopher Porter, CISO of Fannie Mae explains, “I’d describe my program with – get right, get small, see big. Get right is continuously fixing all the things that are broken and building in the culture that it’s OK to find broken things and track them until they’re fixed. Get small is shrinking attack footprint, and consistently doing this across all phases, whether it’s network, data, access. See big is having visibility to proactively and quickly respond and remediate any known security issue that you have.”
Overall, CISOs don’t differ drastically on words they use to describe their programs. When asked if their executives would use similar words, most CISOs believed they would.- Q: What is the impact of Digital Transformation on your program?
- Anderson: “There’s all kinds of things that are wrapped up into digital transformation that we need to pull out and figure out what they mean from a security point of view. Meanwhile, we still have demands from regulators, customers, and our supply chain to be sure we are doing the right thing with our data.”
Porter: “Security has definitely become a little bit more of a culture change in the last few years that I’ve been there, but we’re part of those discussions about protecting that data, but also just the discussion about how long we need to retain that data. It’s my job to ask those questions. Our security journey is wrapped up in the digital product organizations journey to have better customer service and transform the business.”
Raeder: “It’s a race to keep up with digital transformation and everyone wants to take advantage of benefits from digitizing the enterprise. We, as security technologists, have to work alongside IT peers, like the CIOs and CTOs within our organization, to make sure we are part of the strategic planning at the upfront. Security should be working side by side with enterprise functions from the beginning and not coming after the deployment of digital implementations.”
Rushing: “We have been undergoing digital transformation for 7 years now and are on version 9 of our cloud strategy. It has been my job to ensure security is embedded in digital transformation in a frictionless way.”
Scott: “We’ve always been digital. So, what’s interesting now is, what does the next type of digital transformation mean for a company like LinkedIn? I think it’s adoption of additional advanced technologies such as machine learning or AI, determining how those can have an impact on the security of the products that we build and how we can leverage that technology to actually make our products more secure.”
Titus: “Digital transformation is a huge effort that a lot of companies are undertaking. What does digital transformation mean to your organization and how does security overlay into it? How do we overlay security operations to make sure that we’re supporting the business needs as they become more flexible and agile?”
Q: What is the impact of third party risk management?
Anderson: “I think it’s painful for the industry as a whole. Ever since the Target breach, regulators have been scrutinizing third party risk management practices. And especially with digital transformation, we’re going to use more and more partners. The expansion of API’s has also made this very critical to get right. We need to know more about who we trust with our data and the data of our customers and employees.”
Licato: “It’s an additional risk exposure because now their security posture is your security posture. Depending on the criticality of the vendor, it’s really what you need to figure out. You must take a risk-based approach in terms of vendor assessments.”

Levine: “I finally indoctrinated someone on my team to help review the assessments we are asked to complete because I do think they are important. You
have to be able to evaluate the risk and security of your third and fourth parties, but the way we do it today is broken. It’s just not effective. We keep trudging down the same path, and I have yet to see a silver bullet solution to solve this.”
Titus: “Third party vendor risk management is finally getting the type of attention we’ve been hoping it would get, so we’re seeing contract language changes. Also, a lot of changes based on GDPR, so we’re getting more questions starting to filter out of our European theater than we do in the US. The US is still lagging a bit.”
AI and Machine Learning: Fighting Through the Hype

AI and Machine Learning inundate marketing messages, and from the RSA conference to the industry as a whole, they are feeling the hard push of these concepts. Through our interviews, we learned how CISOs are overwhelmed and increasingly alert about security companies touting the AI/Machine Learning message.
When asked about the top trends at the RSA conference, David Levine, CISO of RICOH responded, “AI is definitely a buzz word. The real question is what are companies actually doing regarding AI? In theory, it sounds great, but how do you translate the theory to practicality and put it to good use?”
The bottom line is the majority of CISOs don’t believe, or buy-in to the hype. They question the viability of many security companies actually engaging in true AI and Machine Learning capabilities, showing us how the mania in the market is engendering distrust and extreme caution.
Another factor impacting security leaders is many companies offering different variants of AI capabilities, causing attention when it comes to layering these solutions. Levine continues, “If everybody’s now trying to do machine learning, AI, and behavior analytics, how is this all going to play together/integrate? I think it’s going to be interesting to see how that actually pans out. For example, if you have multiple solutions deployed at different “layers” all utilizing AI/AI variants, and a user calls in and says I can’t get to a particular website, you may have to chase down multiple solutions to figure out which one is trying to declare that it’s a threat of some kind. You can experience this dynamic today to an extent, but multiple solutions all using variants of AI may complicate that process.”
Q: How do you report on metrics and benchmark?
Levine: “Like everybody else, we still struggle with trying to find what the best metrics are to convey to the business. At the end of the day, it’s about knowing your audience, what’s important to them, and what level of detail they like. For example, I do a quarterly governance report where I focus on high-level metrics and initiative updates. I also conduct a Global Information Security report that has far more detailed metrics and operational data.”
Licato: “I have 13 metrics that I look at on a monthly basis that either talk about the effectiveness of the program or operations. I’m trying to keep them at a high level and when we talk about metrics, a lot of people like to see colors. So, we talk about being red, yellow and green, but in a different context. Red would mean management needs to take an immediate action, yellow would mean management needs to monitor this area and green means management does not need to take action at all.”
Porter: “We report metrics to the board quarterly. We also talk to the board about what our target state is, and where we want to be in the next two years. They absolutely want to know how we stack up against others in the industry and whether or not we’re doing the right things.”
Rushing: “I think about two factors. One is collecting true metrics around my program maturity and framework and the ability to define where I am. I need to understand that if I want to move up in maturity what that means from a policy, procedures, and budgetary perspective. The other is technical benchmarking against competitors that I can then use on my own program.”

Scott: “I think it comes down to ensuring objectives are aligned on what the security organization is supposed to bring to the table. At LinkedIn, the focus is on ensuring member trust with the products we build, securing and hardening our infrastructure, and being resilient when bad things happen. It’s really important as a CISO to have a very clear and crisp narrative about what those security objectives are and receive buy in from additional internal stakeholders.”
Titus: “KRI’s are really a great way to do it. Board reporting is a challenge because every board is not created equal. Some companies I’ve worked for have wanted to tell the board everything. Other companies have been more about making sure that we’re giving information that is relevant. Figuring out that balance with your board of how much or how little information is key.”
Q: How do you clear the security product clutter and select the right product for your needs?
Levine: “Step one is to determine what your requirements are, what problem(s) you are trying to solve, and what the business purpose for the product/solution is. Once you have that documented, the field of available options is usually narrowed down. Next, looking at business viability, integration capabilities, and general fitment with your existing tool sets all come in to play. For example, we were recently looking for a Cloud Access Security Broker (CASB) solution. While there are numerous solutions out there, once we evaluated the options based on some very specific requirements we were down to just a few to evaluate.”

Licato: “You must have a process. What is the business, and what are the business goals? First you must align to strategic goals. You have a conversation about who the leaders are, and you start with the leaders. Is it going to enable the business and create less friction for you in your environment? Then for us, it really comes down to getting to know yourself and what you are willing to do.”

Licato: “You must have a process. What is the business, and what are the business goals? First you must align to strategic goals. You have a conversation about who the leaders are, and you start with the leaders. Is it going to enable the business and create less friction for you in your environment? Then for us, it really comes down to getting to know yourself and what you are willing to do.”
Raeder: “I don’t put all my eggs in one basket when it comes to relying on industry publications and reports. Those help me narrow down options, then I depend on reaching out to my peers and talking within my own industry about how they are solving a particular problem. When I do have it narrowed down, getting references within my own space is invaluable. I ask peers how they used the product and what their feedback is on its ability to solve my specific problem. I’ve done this with the last four to five major investments we have made.”
Rushing: “To clear the clutter, you have to look at your own environment and understand how it best functions. I see the biggest thing as people trying to find an ‘easy button’ or some product that is overly simple to leverage and use. It is a nice place to be, but in this world of different options with 2400 security companies, it’s not because they all solve the same thing. You must test your products, see how they fit, that can provide that kind of force multiplier that you want to actually have.”
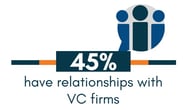
Titus: “Some CISOs are on the more cutting edge and are leaning into some of the newer stuff, and they’ve got the money to be able to bring them in as research partners. But many of us don’t have that capability. So, I’m going to listen to my peers a lot to see what they’re doing. I have to think about what industry they’re in. Are they regulated versus non-regulated and does that make sense for my own industry.”
Q: What impact does GDPR have on your security program?
Anderson: “If you think of the old adage, if you have a good security program, compliance isn’t going to be a problem for you, I think GDPR is a little bit different. It’s really about the privacy of the data and the scope of the data has expanded. How data governance has been approached has varied across industries and programs. Understanding all the data that’s been collected, our rights to the data and how we anonymize it has been and will continue to be quite a big focus at our company and across the financial services industry in general.”
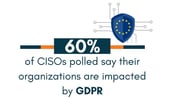
Scott: “GDPR has reinforced the importance of making sure that we adhere to privacy principles about providing our members clarity, consistency, and control. What we’ve done as part of our security program is ensure that all of our products continue to meet that bar and make sure that they’re aligned with the regulatory standards.”
Q: Why are business alignment, revenue generator, and competitive advantage top strategic challenges for CISOs?
Anderson: “We all have finite resources and we need to be sure our security priorities align with our business priorities. I’m lucky to participate in our strategy process which starts with the business.”
Porter: “With impacting revenue, I think it depends on what type of company you are. If you’re a B2C company and you can tie your security technologies and trends that you’re implementing to reduction of fraud, then you can make that play that you’re reducing cost, reducing bottom line. When you’re a B2B company like we are, that’s a bit harder to quantify.”

Titus: “How do you influence up, and then how do you think more broadly about what are the impacts to the business and what are the things that could hurt us from generating revenue?”
Rushing: “If you are not already aligned to the business, you’re late to the party. Where we are today, security should already be aligned and now be a business enabler.”
Market Trend: What are the most cluttered security product spaces?
After walking the RSA conference floor and getting inundated on a daily basis with security product pitches, CISOs made it clear there is an increasing amount of clutter in the market. We spoke with CISOs who told us about the 2,500+ security product companies currently in the marketspace, and how some areas stand out as more cluttered than others.
After walking the RSA conference floor and getting inundated on a daily basis with security product pitches, CISOs made it clear there is an increasing amount of clutter in the market. We spoke with CISOs who told us about the 2,500+ security product companies currently in the marketspace, and how some areas stand out as more cluttered than others.
From colorful, fun booth displays, to creative draws to get people to visit their booths, vendors went above and beyond previous years to stand out in the even more crowded space. The time of ‘one-upping’ the next vendor and investing a tremendous amount of money into marketing and messaging at conferences is ever present.

CISOs we interviewed commented on the increase year-over-year of security companies at the RSA conference (and most other security conferences). For security companies, it is a chance for them to get their product name out there or solidify their place in the market. Newer security companies have a rare opportunity to garner attention and gauge market interest in their offerings.
So, when asked what areas are the most cluttered, the majority of CISOs we interviewed gave the above results.
Endpoint remains to be the top most cluttered space. When asking the CISOs why they think this is the case, they believe the need for endpoint protection remains to be a top concern. Threats continue to increase at an accelerated pace and endpoint vendors are utilizing AI and machine learning in order to keep up. Many CISOs believe threats are proliferating too fast for humans to keep up with in real time.

To clear the clutter and understand what products to invest in, CISOs told us they first identify top players in the space. By doing so, they are able to start with 3-5 leading companies and narrow down from there. They next reach out to their network of security leaders, trusted advisors, and peers. Their networks are prime spaces to discuss others’ experiences using specific products and feedback on real use case practice.
Leveraging a network of security peers enables CISOs to speak with trusted, unbiased sources in order to make their own security product investment decisions. They recommend first doing a detailed research on which products match your business and technical requirements. While many CISOs’ use cases for purchasing a product may be similar, there are instances where they may not be.
Along with endpoint, CISOs we spoke to said Cloud Access Security Brokers, Identity and Access Management, and SIEM to be the other top crowded spaces.
We hope you enjoyed reading our Q&A with leading CISOs. If you are interested in being featured in future trends-based articles, let us know.
[All statistics, graphs, and results in this article are direct property and analytics of K logix]
[All statistics, graphs, and results in this article are direct property and analytics of K logix]
Subscribe
Stay up to date with cyber security trends and more

